Everything Linux, A.I, IT News, DataOps, Open Source and more delivered right to you.
"The best Linux newsletter on the web"
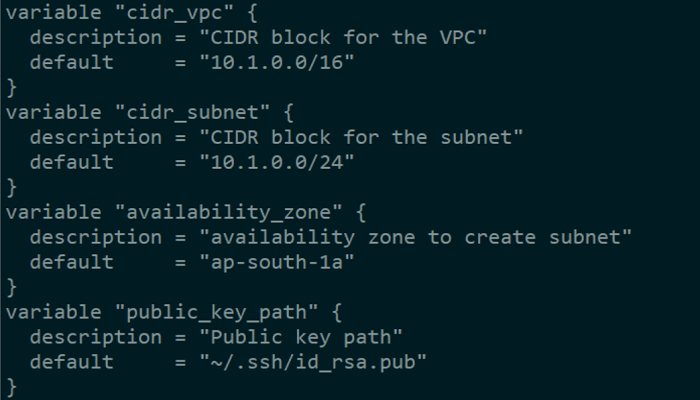
We learned about the terraform variable in the previous article. Let’s start with an example.
Let’s set the terraform provider to AWS with the access key, secret key, and region where we wish to build these resources, as usual.

After we’ve set up the provider, we’ll add all of the variables we’ll need to create our resources.

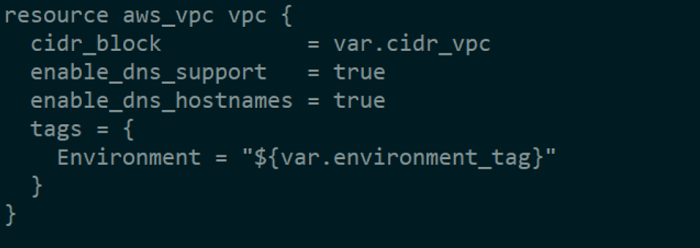
Let’s use our variables one by one to create our resources now that we’ve declared them. We’ll construct a VPC with a defined CIDR block and allow DNS support and DNS hostnames so that each instance has a DNS name in addition to an IP address.

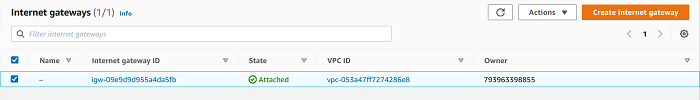
An internet gateway must be deployed to the VPC so that subnets can access the internet from within.

The subnet is added to the VPC and given its own CIDR block, which is a subset of the VPC CIDR block within the availability zone.


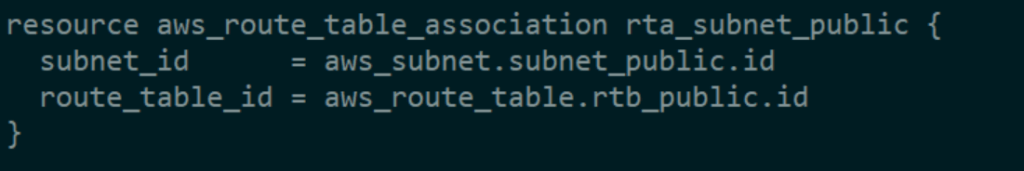
A routing table that uses an internet gateway to reach the internet must be added.


Once the routing table has been constructed, we must link it to the subnet in order to make our subnet public.
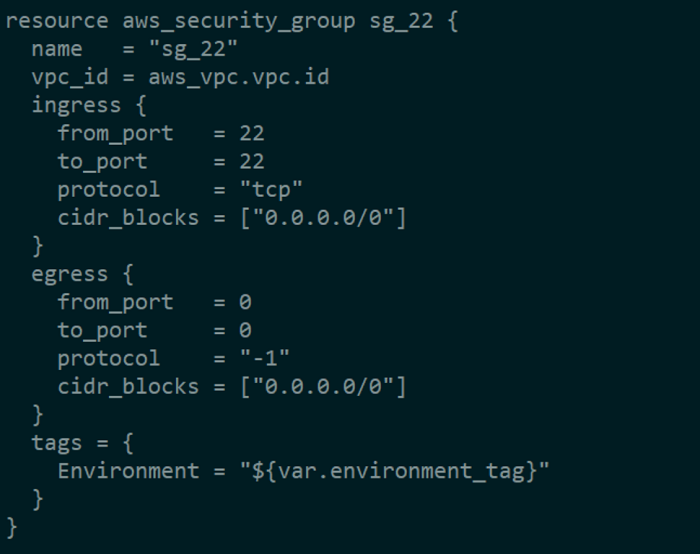
After we’ve set up our networking, we’ll need to build an EC2 instance where we can SSH using port 22. To do so, we’ll need to first construct a security group that can be associated to our EC2 server during setup.
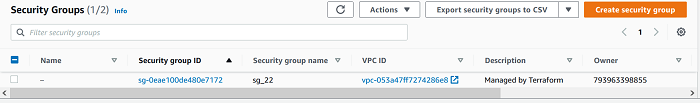
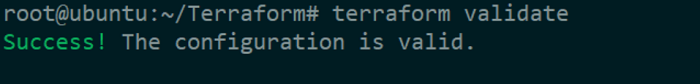
Run the command to validate the code and check if it generates any errors.
$ terraform validate
When you run the terraform plan command, the output will show you which resources will be created, deleted, or updated.
$ terraform plan
Output:
root@ubuntu:~/Terraform# terraform plan
aws_vpc.vpc: Refreshing state… [id=vpc-053a47ff7274286e8]
aws_security_group.sg_22: Refreshing state… [id=sg-0eae100de480e7172]
aws_internet_gateway.igw: Refreshing state… [id=igw-09e9d9d955a4da5fb]
aws_route_table.rtb_public: Refreshing state… [id=rtb-018927bfa7112b64d]
Terraform used the selected providers to generate the following execution plan.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# aws_route_table_association.rta_subnet_public will be created
+ resource "aws_route_table_association" "rta_subnet_public" {
+ id = (known after apply)
+ route_table_id = "rtb-018927bfa7112b64d"
+ subnet_id = (known after apply)
}
# aws_subnet.subnet_public will be created
+ resource "aws_subnet" "subnet_public" {
+ arn = (known after apply)
+ assign_ipv6_address_on_creation = false
+ availability_zone = "ap-south-1a"
+ availability_zone_id = (known after apply)
+ cidr_block = "10.1.0.0/24"
+ enable_dns64 = false
+ enable_resource_name_dns_a_record_on_launch = false
+ enable_resource_name_dns_aaaa_record_on_launch = false
+ id = (known after apply)
+ ipv6_cidr_block_association_id = (known after apply)
+ ipv6_native = false
+ map_public_ip_on_launch = true
+ owner_id = (known after apply)
+ private_dns_hostname_type_on_launch = (known after apply)
+ tags = {
+ "Environment" = "Production"
}
+ tags_all = {
+ "Environment" = "Production"
}
+ vpc_id = "vpc-053a47ff7274286e8"
}
Plan: 2 to add, 0 to change, 0 to destroy.
Run the Apply Command to make these modifications to the infrastructure.
$ terraform apply
Output:
Do you want to perform these actions? Terraform will perform the actions described above. Only 'yes' will be accepted to approve. Enter a value: yes aws_subnet.subnet_public: Creating… aws_subnet.subnet_public: Still creating… [10s elapsed] aws_subnet.subnet_public: Creation complete after 11s [id=subnet-0507b2b236343b77 aws_route_table_association.rta_subnet_public: Creating… aws_route_table_association.rta_subnet_public: Creation complete after 1s [id=rtb] Apply complete! Resources: 2 added, 0 changed, 0 destroyed.
Let’s create a key pair for SSHing into our EC2 instance.
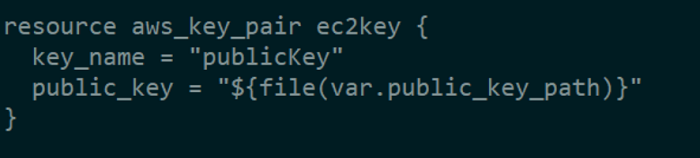
Let’s launch an EC2 instance with our newly established key pair and security group within our public subnet once everything is ready.

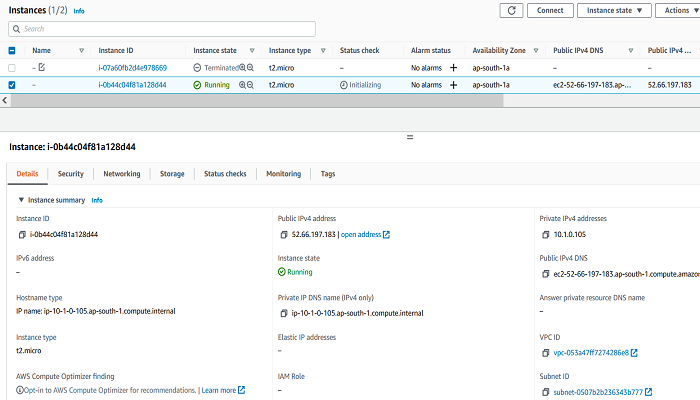
Our EC2 instance is now ready thanks to the terraform code above. We may now use SSH with “ec2-user,” the default user provided by AWS for EC2 instances.
To SSH inside your EC2 instance, replace <Key> with the path to your private key and <IP> with the IP address of your EC2 instance.
$ ssh -i <Key> ec2-user@<IP>This git repository contains the complete code: https://github.com/Singh-1313/AWS_Instance_with_Terraform_VPC
/////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////
Keep Reading About Terraform
Everything Linux, A.I, IT News, DataOps, Open Source and more delivered right to you.
"The best Linux newsletter on the web"