Introduction
Disk encryption protects the data on a block device to be encrypted. To access the device’s decrypted contents, a user must provide a passphrase or key as authentication. It is essential for mobile computers and removable media. In addition, it helps protect the device’s contents even if it has been physically removed from the system. The LUKS format is a default implementation of block device encryption in RHEL.
The Linux Unified Key Setup-on-disk-format (LUKS) enables you to encrypt block devices, and it provides a set of tools that simplifies managing the encrypted devices. LUKS allows multiple user keys to decrypt a master key, which is used for the bulk encryption of the partition.
RHEL utilizes LUKS to perform block device encryption. By default, the option to encrypt the block device is unchecked during the installation. However, if you select the option to encrypt your disk, the system prompts you for a passphrase every time you boot the computer. This passphrase “unlocks” the bulk encryption key that decrypts your partition. If you choose to modify the default partition table, you can choose which partitions you want to encrypt. This is set in the partition table settings.
What LUKS does?
- LUKS encrypts entire block devices and is well-suited for protecting mobile devices contents such as removable storage media or laptop disk drives.
- The underlying contents of the encrypted block device are arbitrary, which makes it helpful in encrypting swap devices. This can also be useful with specific databases that use specially formatted block devices for data storage.
- LUKS uses the existing device mapper kernel subsystem.
- LUKS provides passphrase strengthening, which protects against dictionary attacks.
- LUKS devices contain multiple key slots, allowing users to add backup keys or passphrases.
Install cryptsetup to the server
# dnf install cryptsetup -y
Last metadata expiration check: 0:07:52 ago on Sat 26 Feb 2022 12:58:23 PM UTC.
Dependencies resolved.
=======================================================================================================================
Package Architecture Version Repository Size
=======================================================================================================================
Installing:
cryptsetup x86_64 2.3.3-4.el8 baseos 190 k
Upgrading:
cryptsetup-libs x86_64 2.3.3-4.el8 baseos 470 k
Transaction Summary
=======================================================================================================================
Install 1 Package
Upgrade 1 Package
Total download size: 660 k
Is this ok [y/N]:
Downloading Packages:
(1/2): cryptsetup-2.3.3-4.el8.x86_64.rpm 81 kB/s | 190 kB 00:02
(2/2): cryptsetup-libs-2.3.3-4.el8.x86_64.rpm 173 kB/s | 470 kB 00:02
-----------------------------------------------------------------------------------------------------------------------
Total 242 kB/s | 660 kB 00:02
Running transaction check
Transaction check succeeded.
Running transaction test
Transaction test succeeded.
Running transaction
Preparing : 1/1
Upgrading : cryptsetup-libs-2.3.3-4.el8.x86_64 1/3
Running scriptlet: cryptsetup-libs-2.3.3-4.el8.x86_64 1/3
Installing : cryptsetup-2.3.3-4.el8.x86_64 2/3
Cleanup : cryptsetup-libs-2.3.3-2.el8.x86_64 3/3
Running scriptlet: cryptsetup-libs-2.3.3-2.el8.x86_64 3/3
Verifying : cryptsetup-2.3.3-4.el8.x86_64 1/3
Verifying : cryptsetup-libs-2.3.3-4.el8.x86_64 2/3
Verifying : cryptsetup-libs-2.3.3-2.el8.x86_64 3/3
Upgraded:
cryptsetup-libs-2.3.3-4.el8.x86_64
Installed:
cryptsetup-2.3.3-4.el8.x86_64
Complete!
[root@node1 ~]#
How to configure encrypted storage with LUKS using passphrases
Initialize a LUKS partition with the command: cryptsetup luksFormat device
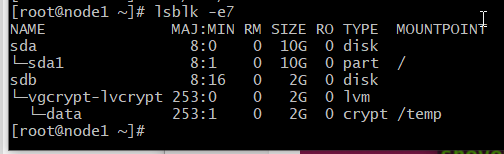
Potential containers for a “LUKS partition”: /dev/sda3, /dev/sdb, /dev/VG/LV, /dev/mapper/mpath1, etc.
From here on in this document, this will be referred to as DEV
# cryptsetup luksFormat /dev/sdb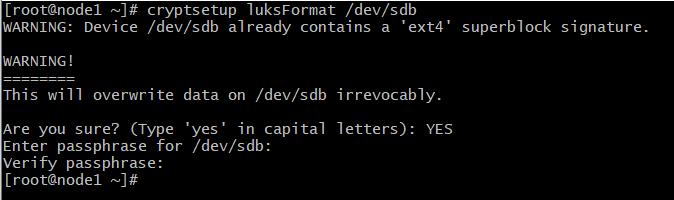
# cryptsetup luksFormat /dev/vgcrypt/lvcrypt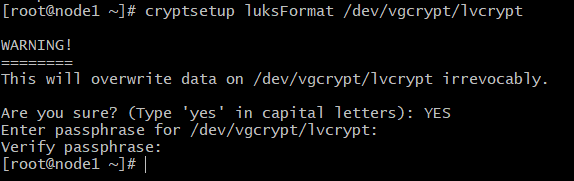
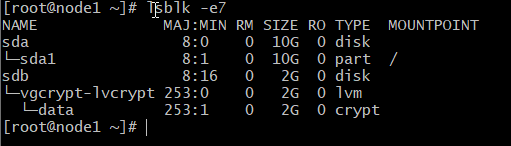
Opening the Encrypted Storage Device Once your storage device /dev/vgcrypt/lvcrypt is encrypted, you can decrypt it and map it as data on your computer with one of the following commands:
# cryptsetup -v open /dev/vgcrypt/lvcrypt data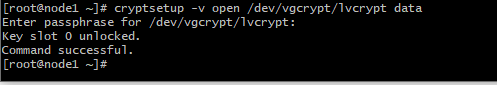
Device data is created and it is of the type crypt.
Creating a Filesystem on the Decrypted Storage Device
Once you’ve decrypted the storage device /dev/vgcrypt/lvcrypt
and mapped it as the data storage device. Then, you can use the mapped storage device data as usual.
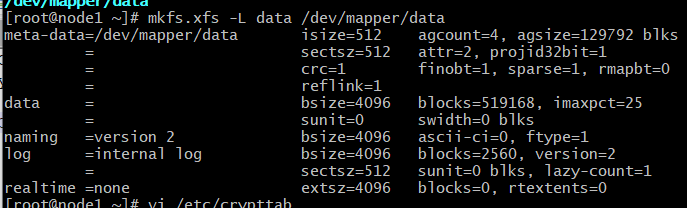
To create an XFS filesystem on the decrypted storage device data, run the following command:
Mounting the Decrypted Filesystem:
Once you’ve created a filesystem on your decrypted storage device data, you can mount it on your computer as usual.
# mount /dev/mapper/data /temp/The decrypted storage device data is mounted on the /temp directory