Introduction
WPScan is a free, for non-commercial use, black box WordPress security scanner written for security professionals and blog maintainers to test the security of their sites.
What can WPScan check for?
- The version of WordPress installed and any associated vulnerabilities
- What plugins are installed and any associated vulnerabilities
- What themes are installed and any associated vulnerabilities
- Username enumeration
- Users with weak passwords via password brute forcing
- Backed up and publicly accessible wp-config.php files
- Database dumps that may be publicly accessible
- If error logs are exposed by plugins
- Media file enumeration
- Vulnerable Timthumb files
- If the WordPress readme file is present
- If WP-Cron is enabled
- If user registration is enabled
- Full Path Disclose
- Upload directory listing
Install WPScan using Ruby gem
Just follow the steps below:
- Install CURL
sudo apt update && sudo apt -y install curl #On Debian/Ubuntu
sudo yum -y install curl #On RHEL/CentOS- Then import the GPG signing.
curl -sSL https://rvm.io/mpapis.asc | gpg --import -
curl -sSL https://rvm.io/pkuczynski.asc | gpg --import -- Install RVM on Linux
Note: RVM (Ruby Version Manager) is a command line tool which allows us to easily install, manage and work with multiple Ruby environments from interpreters to sets of gems.
curl -L get.rvm.io | bash -s stable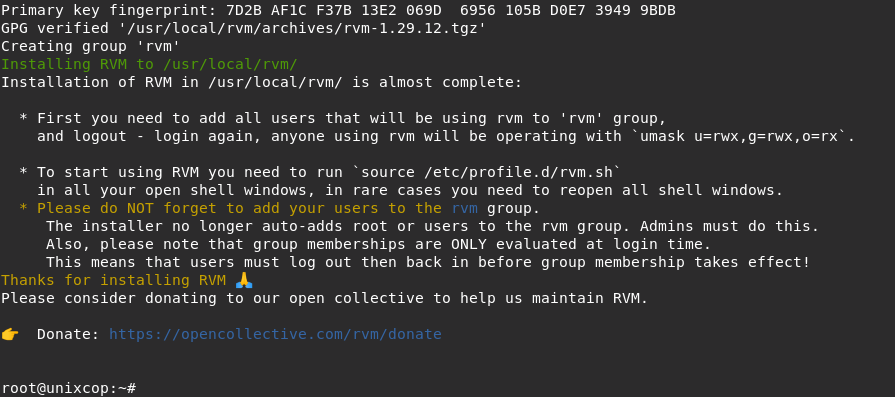
- Source the RVM PATH.
source /home/$USER/.rvm/scripts/rvm- Install Ruby 2.5.8 using RVM.
export RUBY_VER='2.5'
rvm install ${RUBY_VER}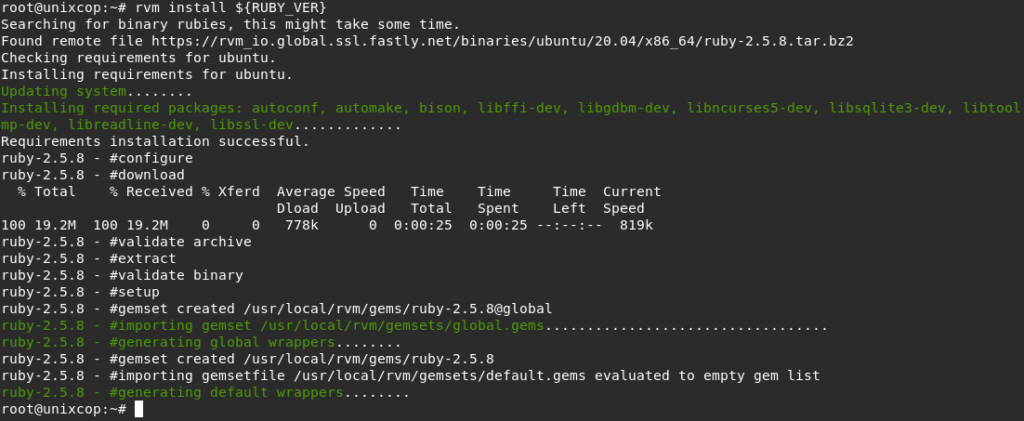
- Use the installed Ruby version as the default.
rvm use ${RUBY_VER} --default- Check the installed Ruby version.
ruby -v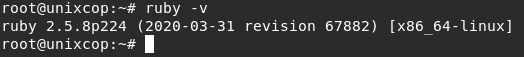
- Install Nokogiri.
Note: Nokogiri is an open source software library to parse HTML and XML in Ruby. It depends on libxml2 and libxslt to provide its functionality.
Note: The last version of nokogiri (>= 0) to support your Ruby & RubyGems was 1.12.5. Try installing it with gem install nokogiri -v 1.12.5
nokogiri requires Ruby version >= 2.6, < 3.2.dev. The current ruby version is 2.5.8.224.
So we will install nokogiri v 1.12.5
gem install nokogiri -v 1.12.5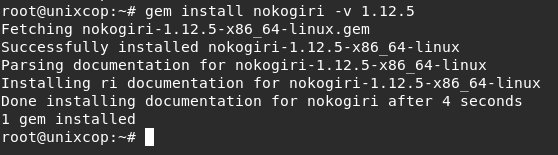
- Install WPScan – WordPress security scanner using RubyGems.
gem install wpscan
- Update wpscan using the command below
gem update wpscan- Check the version of wpscan
wpscan --version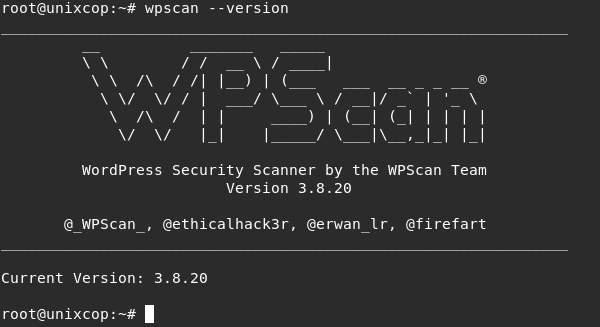
Install WPScan using Docker
- You need to have Docker installed on your system. This can be achieved using the dedicated guide below.
How to install docker on centos 8
How to install Docker CE on Rocky Linux 8
How to install Docker on Debian 11
- With Docker installed and running, add your user to the Docker group.
sudo usermod -aG docker $USER
newgrp docker- Pull the WPScan container image.
docker pull wpscanteam/wpscan- Now you can run WPScan as below.
docker run -it --rm wpscanteam/wpscan [option]How to use WPScan
WPScan can be used to scan vulnerabilities. Note that, the below scans should be performed against your own blog.
1. Scan the entire blog site
To scan the blog, run
wpscan --url wordpress.example.comFor Docker:
docker run -it --rm wpscanteam/wpscan --url wordpress.example.com
WPScan will scan HTTP, if you want HTTPS to be scanned, modify your URL
wpscan --url https://wordpress.example.com -o scan-testThe -o flag can be used to output the scan results in a file.
There are 3 detection modes that can be run on a WordPress site i.e
- aggressive mode – more intrusive scan by sending a thousand request to the server.
- passive mode – send a few requests to the server. This is normally used to scan the homepage.
- mixed(default) – uses both the aggressive and passive modes.
A given detection mode can be specified as below.
wpscan --url wordpress.example.com -o test --detection-mode aggressive2. Scan Vulnerable Plugins.
Check for vulnerabilities in a plugin, the following argument is used:
-e/--enumerate [OPTS] option to the wpscan. The [OPTS] here can be ap for all plugins, vpfor vulnerable plugins and p for plugins.
For example, to scan vulnerable plugins use the command:
wpscan --url wordpress.example.com -e vp3. Scan Vulnerable Themes
Similar to plugins, themes can be scanned using the -e/--enumerate [OPTS]command. But now, [OPTS] is replaced with vt (Vulnerable themes), at (All themes), or t (Themes).
For example, themes with known vulnerabilities can be scanned as below.
wpscan --url wordpress.example.com -e vt4. Password Strength Testing.
To be able to know password strengths, you can try to brute force them. This process may be a bit slow depending on the number of passwords in the password file to be scanned -P, --passwords FILE-PATH, -t, --max-threads VALUE specifies the number of threads.
For example, to brute force the admin user, run the command:
wpscan --url wordpress.example.com -P password-file.txt -U admin -t 50A number of users’ password strengths can be tested without specifying the username.
wpscan --url wordpress.example.com -P password-file.txt -t 505. Enumerate WordPress Users.
To know users who can log in to a site, use the -e/--enumerate u option. Here, u stands for the user IDs.
wpscan --url wordpress.example.com -e u6. Scan WordPress in undetectable mode.
The above scans can as well be performed in stealth mode by adding the argument --stealthy
For example:
wpscan --url wordpress.example.com --stealthyIn case you need help when using WPScan, find help as below.
wpscan -h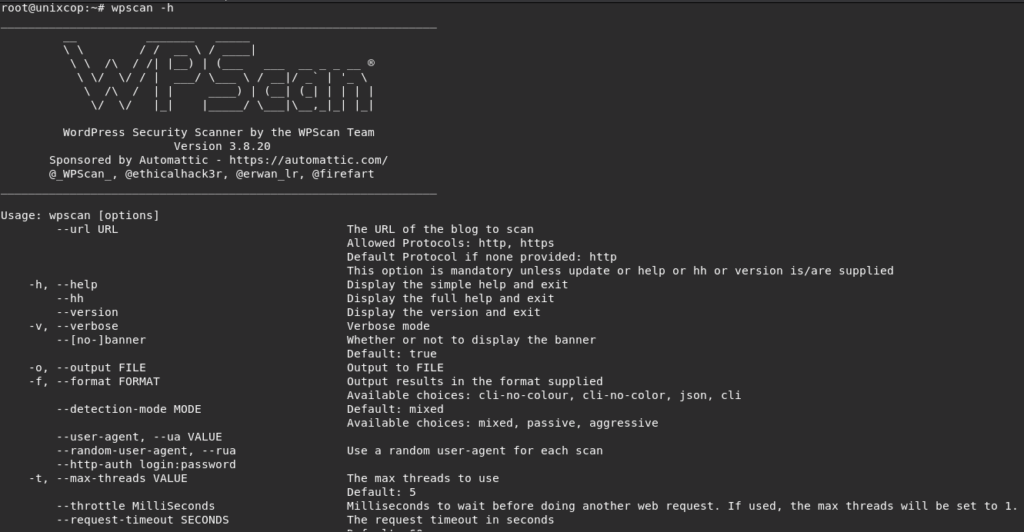
Conclusion
That is it!
We showed you how to install and use WPScan – WordPress security scanner.
Thanks.



