Today I will shoy some SSH Tips and Tricks
SSH Tips and Tricks
The following articles lists some of the various tips and tricks I have learned about OpenSSH client from the internet. This is by no means an exhaustive list so feel free to suggest some more in the comments.
Host Configuration
OpenSSH allows configuring the client on a per-host basis. This is done in the $HOME/.ssh/config file, which takes precedence over the system-wide /etc/ssh/ssh_config.
For example, there are two ways to connect with a host named foo.com on port 1337 with the username bar. I can either specify all of this manually with command-line options. Or I can specify it in ~/.ssh/config as follows:
Host foo
HostName foo.com
User bar
Port 1337Furthermore, now I can just do ssh foo as the client will automatically handle all of the options for me. We can also use wildcards for the Host section. For example, if I want to use the same port for every subdomain in the foo.com zone, then I could do this:
Host *.foo.com
Port 1337Command-line Options
We can specify the username on the remote machine to which we’re connecting with either the -l flag or the user@host syntax. However, if the username is same on both machines, then we can omit specifying the username altogether. So if I want to ssh into the host 192.168.1.10 with the username pratik as the user pratik from my machine, then I can just do:ssh 192.168.1.10
Some options don’t have commandline flags. In that case, we can use the -o flag. So, if I need ssh to use a source IP address other than the primary, then I will need to do it with the BindAddress option. The BindAddress option has no commandline flag. Therefore, I’ll have to do it this way:ssh -o BindAddress=<ip> <host>
Another useful feature of OpenSSH is the ability to do X-Forwarding. We can enable X-Forwarding for a host with the -X flag. Since, all of the GUI elements will also get transmitted over the network, this can consume more bandwidth. In that case, we can ask ssh to use compression with the -C flag giving us higher throughput. So, the following would be a good way to use ssh if you want to do X-Forwarding:ssh -X -C <host>
We can also specify jump hosts with the -J flag. Jump hosts act as an intermediate host letting us use an ssh server as a relay to connect to a second ssh server. The following example shows using the 192.168.1.11 server as a jump host to connect to the server at 192.168.1.12:
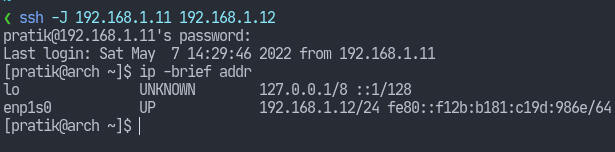
As you can see, it first tried to login to 192.168.1.11 but the final ip addr command shows I’m logged in at 192.168.1.12.
Finally, use the -G flag to make ssh output the current configuration and exit.
Hashing the known_hosts file
Whenever you ssh into a server, it saves the server’s fingerprint in the $HOME/.ssh/known_hosts file. It contains the hostname or IP address of the server along with the fingerprint string. However, the known_hosts file can also disclose the ssh servers to be used by intruders as their targets.
OpenSSH allows us to hash the entries in the known_hosts file so that we can prevent snooping. This is enabled with the HashKnownHosts yes keyword in the client’s configuration. However, this doesn’t hash existing entries. Use ssh-keygen -H to also hash the existing entries in the known_hosts file.
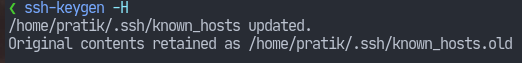
Remember to delete .ssh/known_hosts.old to ensure privacy of hostnames.
Multiplexing
Some SSH connections can take a long time to open. This can be due to various reasons, but having this delay can be a nuisance especially when you try to open multiple ssh sessions. OpenSSH supports connection multiplexing so that we can run multiple ssh sessions over a single TCP connection.
On Unix, this is achieved through sockets. Everything being a file on Unix, our socket will also need to reside somewhere on our filesystem. So let’s set that up.
Let’s dedicate a directory in our $HOME/.ssh/ folder specifically for sockets.
mkdir ~/.ssh/sockets/
Ensure secure permissions.
chmod 700 ~/.ssh/sockets/
Now we can enable multiplexing in the ~/.ssh/config file:
Host *
ControlMaster auto
ControlPath ~/.ssh/sockets/%u@%h:%pThe ControlPath keyword let’s us specify the path of the sockets. The %u, %h and %p are what’s called tokens and specify the remote username, hostname and the port respectively.
Hope these SSH Tips and Tricks will help you on your work.



