This post is about Security Auditing with Lynis
Introduction
I originally intended to write about how to secure a server/workstation system. However, I changed my mind after realising that there is already this battle-tested tool called lynis that does the auditing for us and also
provides us suggestions.
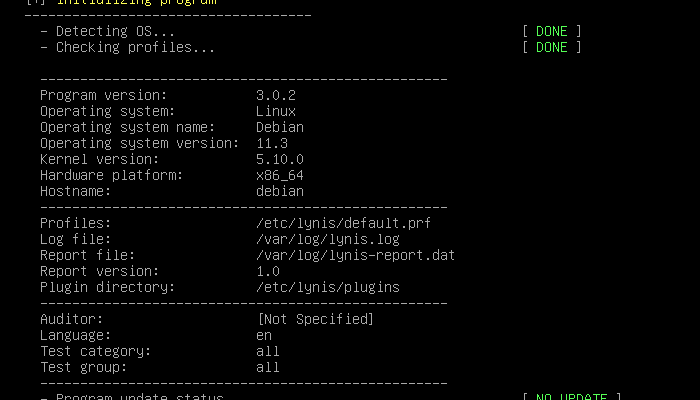
Lynis is a security auditing tool for Unix-based operating systems. In this article, I am going to inspect my default installation of Debian 11 with lynisand try to secure. Lynis performs an in-depth scan of the system. This includes basic checks like permissions in the filesystem to even performing specific tests of the software and libraries that are installed on a system.
This way, it only uses and tests the components concerned with the system on which it is scanning. As an example, for a web server it will only include the web-service related tests after doing the general checkup.
Security Auditing with Lynis – Installation and Performing Audits
Lynis is a popular software. As such, we easily install it on various systems. On Debian, I can install it using apt:
doas apt install -y lynis
Now time for the trying it out. We are provided with a bunch of commands. We can read about them from its manual page. To ask lynis to perform a system audit run:
sudo lynis audit system
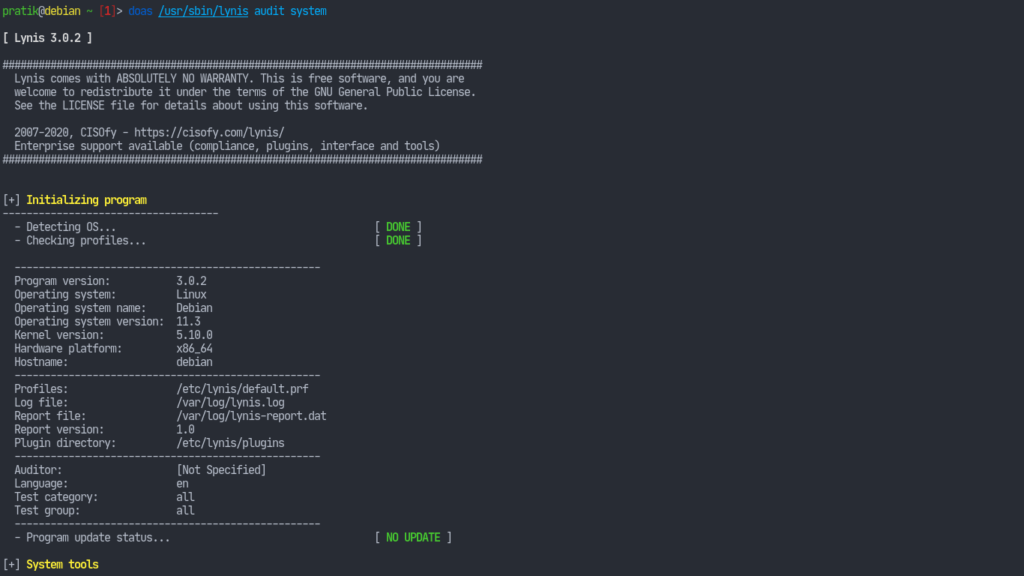
This will take some time.
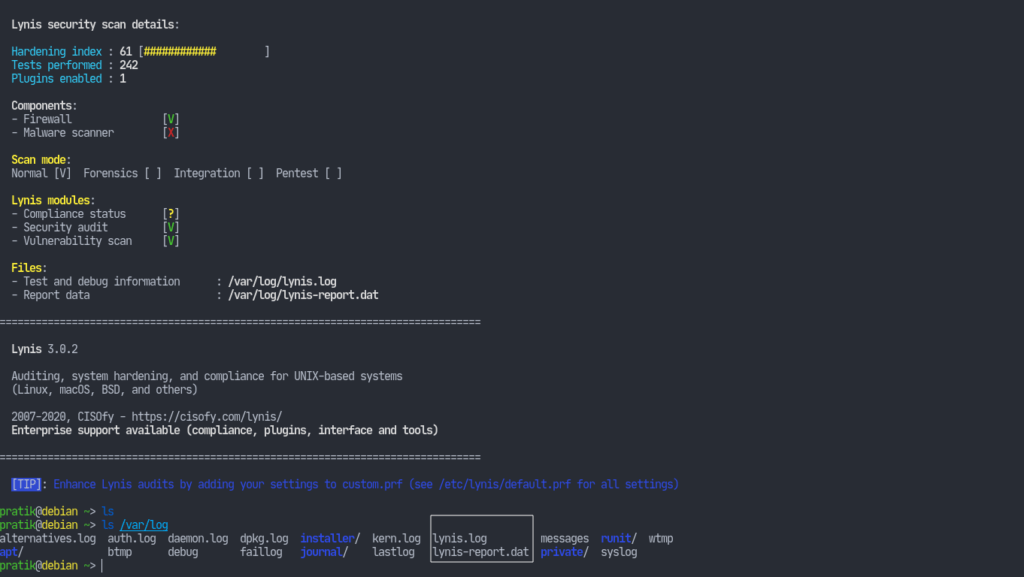
Lynis gives our system a score of 61, which means it needs some work. It has also provided us two log files for us to look at. The lynis.log stores all the technical details of the scan and the lynis-report.dat contains the warnings and suggestions for us to look at. So, let’s look over what suggestions lynis has given us. There are going to be tons of suggestion.
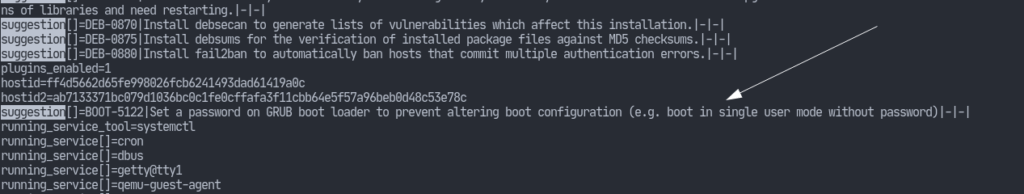
Setting a Bootloader Password
One of the suggestions lynis provides here is to set a bootloader password. It’s common knowledge that you can go to your bootloader menu, modify the kernel parameters setting init=/bin/bash and easily reset your root password. Sometimes, this may pose as a security threat. We may want to ensure that no unauthorized principal can change the boot parameters. Provided, setting a bootloader password doesn’t necessarily guarantee everything. It’s a required level in the multiple levels of security that a system should have.
We have previously covered this topic on our blog. However, technology is quickly evolving and some commands have been outdated. Therefore, I will just include the latest techniques here.
Here’s how you set a password for grub. Run the grub-mkpasswd-pbkdf2 command, and provide a password.
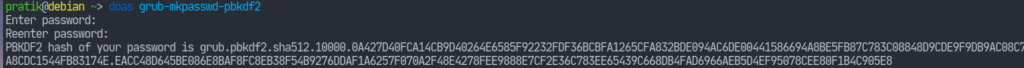
Now copy the text that grub says is your password and append the following to /etc/grub.d/40_custom, replacing the appropriate values:
set superusers="<username>"password_pbkdf2 <username> <copied password>
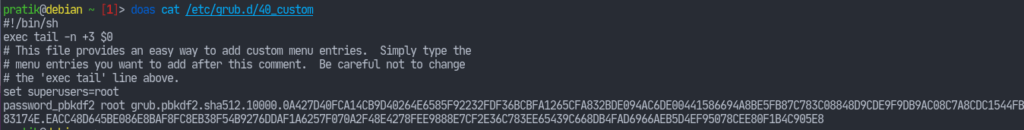
Now change the permissions of the config file so that it’s modifiable only by root (doas is just like sudo):
doas chmod 600 /etc/grub.d/40_custom
Regenerate the grub config files:
doas grub-mkconfig -o /boot/grub/grub.cfg
Then if we reboot the system and try to modify the boot parameters by entering e on the bootloader menu, GRUB shall prompt us for the username and password.
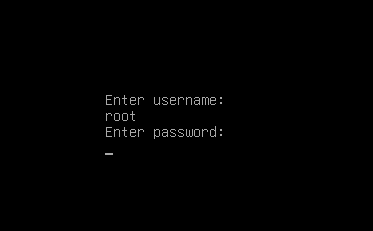
Securing a system is a very lengthy process. Ergo, I have decided to not cover all of the suggestions that Lynis has given me in this single article. Rather, this will be kind of like a multi-part series of articles where I go over the suggestions given by lynisand proceed to secure my system further. That’s it for now; stay tuned for more!