Introduction
So, this tutorial provides step-by-step instructions on recovering/reset lost or forgotten RHEL 8 / CentOS 8 Linux root administrative passwords. To first boot to the set GRUB password and usernames required. So that non-authorized users cannot modify the grub entry at the boot loader stage. Also, check setting up grub for Ubuntu.
Why should we protect set grub password Linux boot loader ?
The primary reasons for password protecting Linux boot loader:
1. Stop Access to Single User Mode – If an attacker can boot into single-user mode, he becomes the root user.
2. Stop Access to the GRUB Console – If the machine uses GRUB as its boot loader, an attacker can use the GRUB editor interface to change its configuration or to gather information using the cat command.
3. Stop Access to Non-Secure Operating Systems – If it is a dual-boot system, an attacker can select at boot time an operating system, such as DOS, which ignores access controls and file permissions.
Generate password for the grub
So, use grub2-setpassword to set a password for the root user:
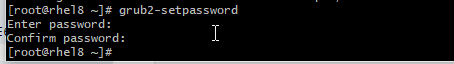
# grub2-setpasswordThe generated password is located at /boot/grub2/user.cfg.
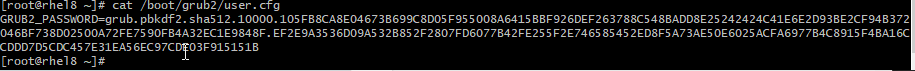
# cat /boot/grub2/user.cfgRecreate the grub config with grub2-mkconfig to set grub password
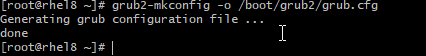
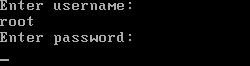
# grub2-mkconfig -o /boot/grub2/grub.cfgReboot the server and verify
# rebootNote: All defined grub menu entries will now require entering user & password each time at boot. The system will not boot without direct user intervention from the console. Prompted for the user, enter “root”.
So, to remove the grub password, visit the red hat site. GRUB 2 configuration file, grub.cfg, is generated during installation, or by invoking the /usr/sbin/grub2-mkconfig utility, and is automatically updated by grubby each time a new kernel is installed. When regenerated manually using grub2-mkconfig, the file is generated according to the template files located in /etc/grub.d/, and custom settings in the /etc/default/grub file.



