Firewalld Introduction
Firewall is a way to protect machines from any unwanted traffic from outside. It provides the power to users to control incoming network traffic on host machines by defining a set of firewall rules. It is in use to allow or deny specific service/port to specific host or network.
Firewalld
Firewalld is a firewall service daemon that provides a dynamic customizable host-based firewall with a D-Bus interface. It performs a dynamic behavior, it means when the rules got change then it enables creating, changing, and deleting the rules without the necessity to restart the firewall daemon each time.
firewalld with nftables backend does not support passing custom nftables rules to firewalld, using the --direct option.
Basic things to know first:
package and service name : firewalld
Command Line Tool: firewall-cmd
Gui-tool: firewall-config
Steps to working with Firewalld
First you need to check the package availability on the server. By default it is available.
[root@localhost ~]# rpm -qa firewalld
firewalld-0.6.3-7.el8.noarch
If you need to install package. Incase it is not available by default.
# yum install firewalld -y
After installation you need to start and enable the service.
# systemctl start firewalld
To make firewall service remain active after system reboot you need to enable it.
# systemctl enable firewalld
To check the running status of firewall servic e
# systemctl status firewalld
or we can check this by command-line tool
# firewall-cmd --state
To stop firewalld service use below command
# systemctl stop firewalld
To prevent firewalld from starting automatically at system start:
# systemctl disable firewalld
Zones
firewalld separates all incoming traffic into zones, with each zone having its own set of rules. To check which zone to use for an incoming connection, firewalld uses this logic, where the first rule that matches wins:
- If the source address of an incoming packet matches a source rule setup for a zone, that
packet will be routed through that zone. - If the incoming interface for a packet matches a filter setup for a zone, that zone will be
used. - Otherwise, the default zone is used. The default zone is not a separate zone; instead, it
points to one of the other zones defined on the system. Unless overwritten by an administrator or a NetworkManager configuration, the default zone for any new network interface will be set to the public zone.
A number of predefined zones are shipped with firewalld, each with their own intended usage:
Default Configuration of firewalld Zones
| Zone Name | Default configuration |
| trusted | Allow all incoming traffic |
| home | Reject incoming traffic unless related to outgoing traffic or matching the ssh, mdns, ipp – client, samba- client, or dhcpv6 – client predefined services. |
| internal | Reject incoming traffic unless related to outgoing traffic or matching the ssh, mdns, ipp – client, samba- client, or dhcpv6 – client predefined services (same as the home zone to start with). |
| work | Reject incoming traffic unless related to outgoing traffic or matching the ssh, ipp – client, or dhcpv6 – client predefined services. |
| permit | Reject incoming traffic unless related to outgoing traffic or matching the ssh or dhcpv6 – client predefined services. The default zone for newly added network interfaces. |
| external | Reject incoming traffic unless related to outgoing traffic or matching the ssh predefined service. Outgoing IPv4 traffic forwarded through this zone is masqueraded to look like it originated from the IPv4 address of the outgoing network interface. |
| dmz | Reject incoming traffic unless related to outgoing traffic or matching the ssh predefined service. |
| block | Reject all incoming traffic unless related to outgoing traffic. |
| drop | Drop all incoming traffic unless related to outgoing traffic (do not even respond with ICMP errors). |
To make a zone active, at least one attribute should be available.
interfaces:
or
sources:To fetch all available zones
[root@localhost ~]# firewall-cmd --get-zones
block dmz drop external home internal libvirt public trusted workCommand to set the default zone.
[root@localhost ~]# firewall-cmd --set-default-zone=work
success
[root@localhost ~]#
Command to check the available default zone.
[root@localhost ~]# firewall-cmd --get-default-zone
work
[root@localhost ~]#
To add service.
firewall-cmd --add-service=<service name>
above command is use to allow traffic to <service> If no – – zone=option is provided, the default zone will be used.
To Remove from the allowed list for the zone. If no – – zone=option is provided, the default zone will be used.
firewall-cmd --remove-service=<service name>
Modify Firewall settings in runtime and permanent configuration
To test the settings before you apply them to the permanent mode. First make changes in settings and then make them permanent.
# firewall-cmd <options>
# firewall-cmd --runtime-to-permanentTo make setting permanent you need to reload the firewall.
# firewall-cmd --permanent <options>
# firewall-cmd --reloadHere are some set of commands that are frequently used with firewall-cmd.
| firewall-cmd Commands | Explanations |
| – – get – services | List all predefined services. |
| – – get – active – zones | List all zones currently in use (have an interface or source tied to them ),along with their interface and source information. |
| – – add – source=<CIDR> [- – zone=<zone>] | Route all traffic coming from the IP address or Network/netmask to the specified zone. If no – – zone= option is provided, the default zone will be used. |
| – – remove – source=<CIDR> [- – zone=<zone>] | Remove the rule routing all traffic coming from the IP address or network/netmask from the specified zone. If no –zone=option is provided, the default zone will be used. |
| – – add – interface=<Interface>[- – zone= <zone>] | Route all traffic coming from <interface>to the specified zone. If no – – zone= option is provided, the default zone will be used. |
| – – change – interface=<Interface>[- – zone= <zone>] | Associate the interface with <zone> instead of its current zone. If no – – zone= option is provided, the default zone will be used. |
| – – list – all [- – zone=<zone>] | List all configured interfaces, sources, services, and ports for <zone>. If no – – zone= option is provided, the default zone will be used. |
| – – list – all- zones | Retrieve all information for all zones (interfaces, sources, ports, services, etc.). |
| – – remove- service=<service> | Remove <service> from the allowed list for the zone. If no – – zone= option is provided, the default zone will be used. |
| – – add – port=<port/protocol> | Allow traffic to the<port/ protocol> port(s). If no – – zone= option is provided, the default zone will be used. |
| – – remove – port=<port/protocol> | Remove the<port/protocol> port(s) from the allowed list for the zone. If no – – zone= option is provided, the default zone will be used. |
For Example:
Let suppose you need to add http service to firewall.
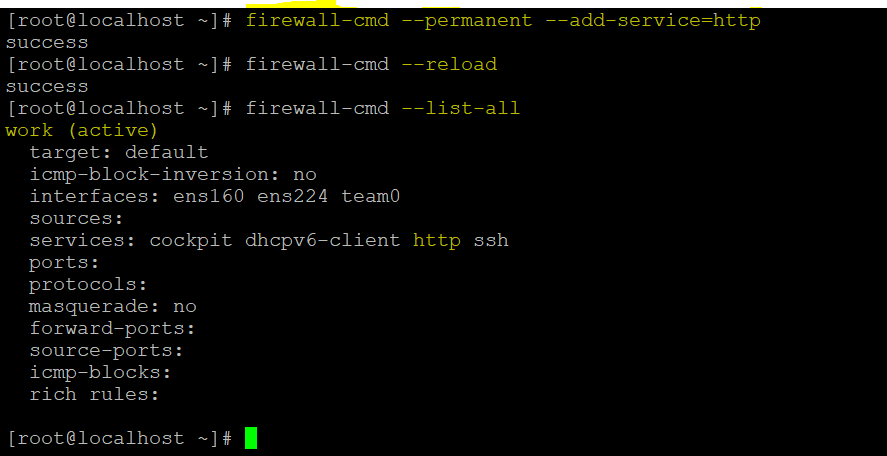
In the above example you can see that we have added http service. we have not provided any zone in above example. So the service added into default active zone(work).
We have used – – permanent option to make these settings permanent. After that we reload it.
Port Forwarding
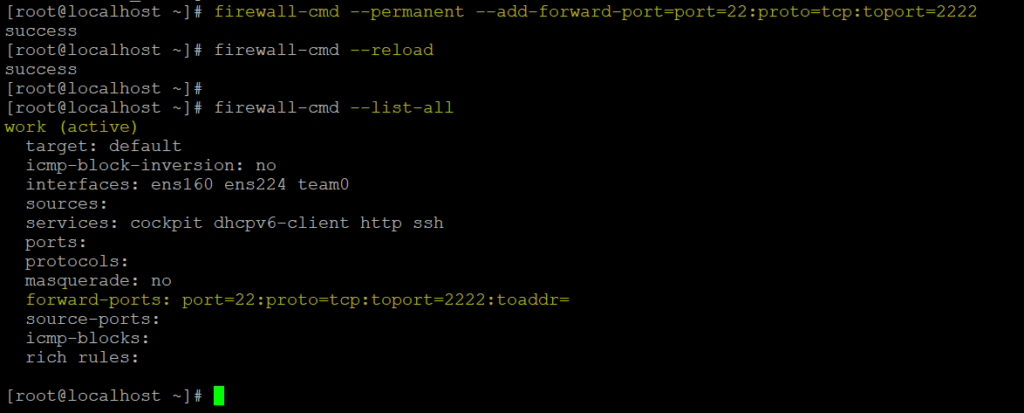
To forward traffic of one port to another port is know as port forwarding. Let suppose you want to forward all traffic of ssh from port 22 to port 2222. then first you need to mention port number in /etc/ssh/sshd_config. After that you will forward that port by below command:
# firewall-cmd --permanent --add-forward-port=port=22:proto=tcp:toport=2222
# firewall-cmd --reload
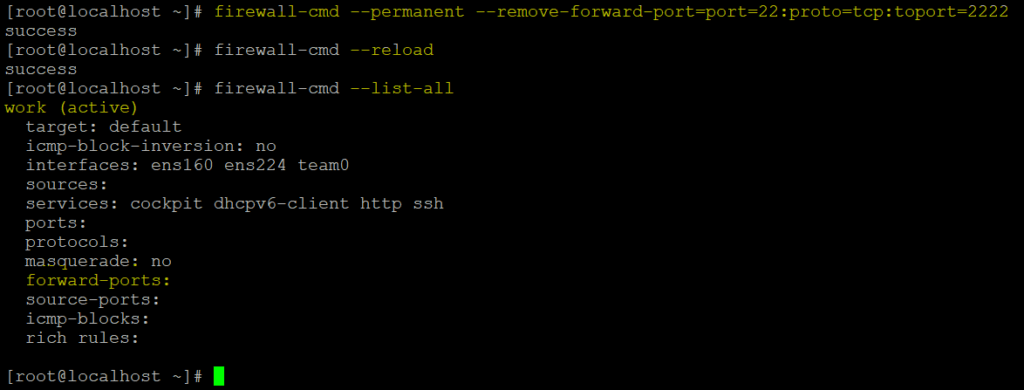
To remove port forwarding.
# firewall-cmd --permanent --remove-forward-port=port=22:proto=tcp:toport=2222
# firewall-cmd --reload
In this article we have discussed about firewalld, zone, and port forwarding. The best way to forward the traffic can be possible by rich-rules. In the next article we will discuss about rich rules on firewall.
Please give your comment and suggestions below. Thank you.