In this post, you will learn how to Export Your Servers Logs with Rsyslog in Centos 8
In this article, we’ll walk through setting up a CentOS/RHEL 8 Rsyslog daemon to deliver log messages to a remote Rsyslog server. This configuration ensures that disc space on your machine is available for other purposes.
In CentOS 8, the Rsyslog daemon is already installed and operating by default. Issue the following commands to see if the rsyslog service is active on the system.
# grep rsyslog | rpm –q # rsyslogd –v 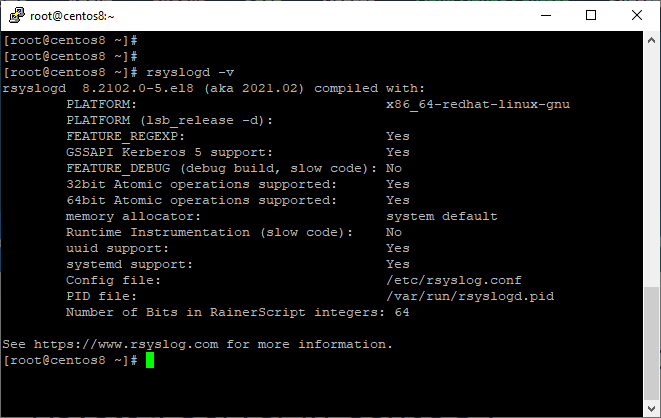
If the Rsyslog package is not installed on your CentOS system, run the command below to install it.
# yum install rsyslogExport Your Servers Logs with Rsyslog
Modify the rsyslog configuration file as follows to force the Rsyslog daemon installed on a CentOS 8 system to function as a log client and send all locally generated log messages to a distant Rsyslog server:
To begin altering, open the main configuration file:
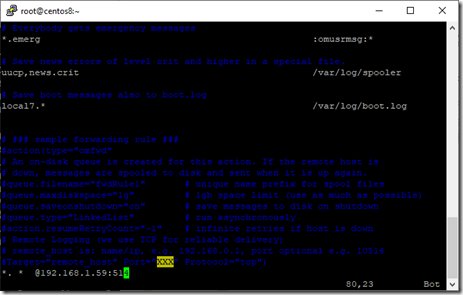
# vim /etc/rsyslog.confThen, as shown in the excerpt below, append the following line to the end of the file.
# *. * @192.168.1.59:514Make sure the IP address and FQDN of the remote rsyslog server are replaced appropriately in the above line. The preceding line tells the Rsyslog daemon to send all log messages to the IP 192.168.1.59 over the 514/UDP port, regardless of facility or severity.
Add another @ character in front of the remote host if the remote log server is configured to only accept TCP connections or if you want to utilise a dependable transport network protocol like TCP, as illustrated in the example below:
# *. * @@logs.domain.lan:514Special characters, such as = or!, can be prefixed to priority levels in Linux rsyslog to signal “this priority only” for equal sign and “not this priority or higher than this” for!
Below are some examples of Rsyslog priority level qualifiers:
kern.info = Kernel logs with a priority of information or higher.
kern.=info = Only kernel messages with the priority of information are allowed.
kern.info;kern.!err = Only kernel messages with the priorities info, notice, and warning are allowed.
kern.debug;kern.!=warning = Except for warning, all kernel priority are equal.
kern.* = All messages with a priority in the kernel
kern.none = Regardless of priority, do not log any associated kernel facility messages.
For example, if you just want to send a subset of facility messages to a remote log server, such as all associated mail messages regardless of priority, add the following line to the rsyslog configuration file:
# mail.* @192.168.1.59:514Finally, in order for the updated settings to take effect, the Rsyslog service must be restarted with the following command:
# systemctl restart rsyslog.serviceIf the Rsyslog daemon is not activated during boot time for some reason, run the command following to enable the service system-wide:
# systemctl enable rsyslog.serviceSend Web Server Logs to a Remote Log Server
By adding the following line to Apache’s main configuration file, as shown below, the HTTP server can be configured to transmit log messages to a remote syslog server.
# vim /etc/httpd/conf/httpd.confOn Apache main conf file add the below line.
CustomLog "| /bin/sh -c '/usr/bin/tee -a /var/log/httpd/httpd-access.log | /usr/bin/logger -thttpd -plocal1.notice'" combinedThe line tells the HTTP daemon to write log messages to the filesystem log file, but it also tells it to send them to a faraway syslog server by designating them as coming from the local1 facility.
If you wish to send Apache error log messages to a remote syslog server as well, create a new rule similar to the one given above, but change the name of the httpd log file and the severity level of the log file to match the error priority, as shown in the following example:
ErrorLog "|/bin/sh -c '/usr/bin/tee -a /var/log/httpd/httpd-error.log | /usr/bin/logger -thttpd -plocal1.err'"After you’ve changed the above lines, you’ll need to restart the Apache daemon to see the changes take effect:
# systemctl restart httpd.serviceBy adding the following lines of code to a nginx configuration file, the Nginx web server has built-in capability to directly log its messages to a remote syslog server as of version 1.7.1.
error_log syslog:server=192.168.1.59:514,facility=local7,tag=nginx,severity=error;
access_log syslog:server=192.168.1.59:514,facility=local7,tag=nginx,severity=info main;/code>To receive the logs sent by the Apache web server, make the following changes to the rsyslog configuration file on the remote Rsyslog server.
local1.* @Apache_IP_address:514That concludes our discussion. You’ve successfully setup the Rsyslog daemon to run in client mode, as well as directed Apache or Nginx to route log messages to a remote syslog server.
If your system breaks, you should be able to figure out what went wrong by looking at the contents of the log files saved on the remote syslog server.
Now you know how to export Your Servers Logs using Rsyslog.
Check out our homepage for more guides




Hello,
Thanks for this article, it is very helpful.
However, i have a question concerning this line “local1.* @Apache_IP_address:514”
Do we have to configure it on the remote server or on the client (with the IP of the remote log server) ?