Introduction
OpenConnect VPN is not officially supported by or associated in any way with Cisco Systems, Juniper Networks, Pulse Secure, Palo Alto Networks, F5, Fortinet, or any of the companies whose protocols we may support in the future. It just happens to interoperate with their equipment. Trademarks belong to their owners in a somewhat tautological and obvious fashion.
An openconnect VPN server (ocserv), which implements an improved version of the Cisco AnyConnect protocol, was also written.
OpenConnect VPN server is an SSL VPN server that is secure, small, fast, and configurable. It implements the OpenConnect SSL VPN protocol and has also (currently experimental) compatibility with clients using the AnyConnect SSL VPN protocol. The OpenConnect protocol provides a dual TCP/UDP VPN channel and uses the standard IETF security protocols to secure it. The OpenConnect client is multi-platform and available here. Alternatively, you can try connecting using the official Cisco AnyConnect client (Confirmed working on Android). For the HAproxy tutorial, you can try the link.
OpenConnect is released under the GNU Lesser Public License, version 2.1.
Development
OpenConnect was started after a trial of the Cisco AnyConnect client under Linux found it to have many deficiencies:
- Inability to use SSL certificates from a TPM or PKCS#11 smartcard, or even use a passphrase.
- Lack of support for Linux platforms other than i386.
- Lack of integration with NetworkManager on the Linux desktop.
- Lack of proper (RPM/DEB) packaging for Linux distributions.
- “Stealth” use of libraries with dlopen(), even using the development-only symlinks such as libz.so — making it hard to properly discover the dependencies which proper packaging would have expressed
- Tempfile races allowing unprivileged users to trick it into overwriting arbitrary files, as root.
- Unable to run as an unprivileged user, which would have reduced the severity of the above bug.
- Inability to audit the source code for further such “Security 101” bugs.
Basic image features
- Base: Alpine
- Latest OpenConnect Server 8.04
- Size: 20MB
- Modification of the listening port for more networking versatility
- Customizing the DNS servers used for queries over the VPN
- Supports tunneling all traffic over the VPN or tunneling only specific routes via split-include
- Config directory can be mounted to a host directory for persistence
- Create certs automatically using default or provided values, or drop your own certs in /config/certs
- Advanced manual configuration for power users
- FREE VPN server can be connected from the link
Basic Configuration
Without customizing cert variables
# podman run --privileged --name openconnect-server -d \
> -p 8888:8888 -p 8889:8889 -e OPENCONNECT_URL=vpn.gateway.com \
> wazum/openconnect-proxy:latestWith customizing cert variables
# podman run --privileged --name openconnect-server -d \
-p 8888:8888 -p 8889:8889 -e OPENCONNECT_URL=vpn.gateway.com \
-e OPENCONNECT_USER=unixcop -e OPENCONNECT_PASSWORD=unixcop wazum/openconnect-proxy:latest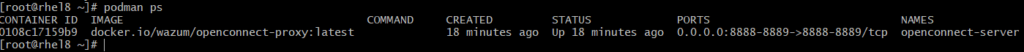
Use container with docker-compose
vpn:
container_name: openconnect_vpn
image: wazum/openconnect-proxy:latest
privileged: true
env_file:
- .env
ports:
- 8888:8888
- 8889:8889
cap_add:
- NET_ADMIN
networks:
- mynetwork
Set the environment variables for openconnect in the .env file again (or specify another file) and map the configured ports in the container to your local ports if you want to access the VPN on the host when running your containers. Otherwise, only the docker containers in the same network have access to the proxy ports.
Route traffic through VPN container
Let’s say you have a vpn the container defined as above, then add network_mode option to your other containers:
depends_on:
- vpn
network_mode: "service:vpn"Keep in mind that networks, extra_hosts, etc. and network_mode are mutually exclusive.
Configure proxy
The container is connected via openconnect, and now you can configure your browser and other software to use one of the proxies (8888 for HTTP/HTTPS or 8889 for socks).
For example, FoxyProxy (available for Firefox, Chrome) is a suitable browser extension.
You may also set environment variables:
# export http_proxy="http://127.0.0.1:8888/"
# export https_proxy="http://127.0.0.1:8888/"Open browser and configure the vpn/proxy
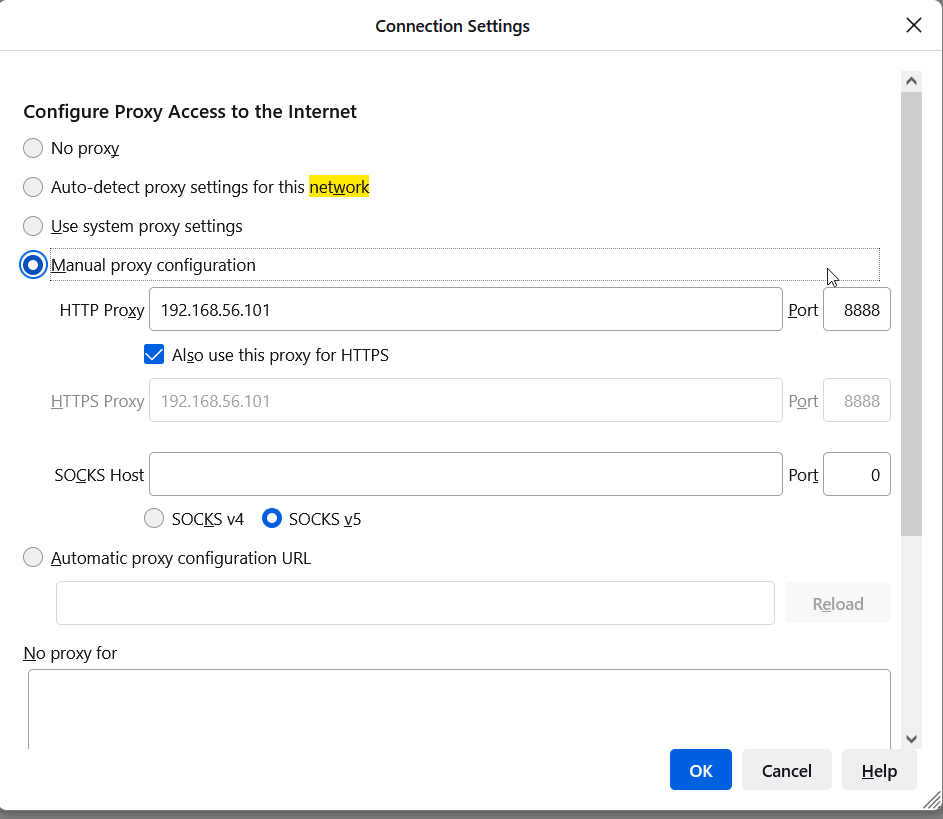
We have a secured vpn and proxy