The following guide explains how to use the Google Authenticator PAM module on Ubuntu for both SSH and sudo authentication. Usernames and passwords can undoubtedly be broken utilizing plenty of hacking methods. So, any organization or element that seriously treats security needs to carry out 2-Factor confirmation.
In addition to the conventional password provided. An extra layer of authentication will be added for SSH. That extra layer will be Google authenticator. Where using google authenticator the password will be generated on your mobile device. This will add an extra layer of security while accessing your server using SSH. This two-factor authentication system will improve the security liability of the server or other related resources.
So, in our scenario, we will be using SSH and Ubuntu 21.04 for demonstration purposes. A smart device installed with Google Authenitcator is required, android in our case.
Let’s go step by step.
Installation
First, we will install Google authenticator on a mobile device first.
After installing the mobile app on your android device, you can start. Now we are ready to bind any device with a google authentication system or PAM.
So, Let’s install Authenticator to Ubuntu 21.04 as well. Have a look.
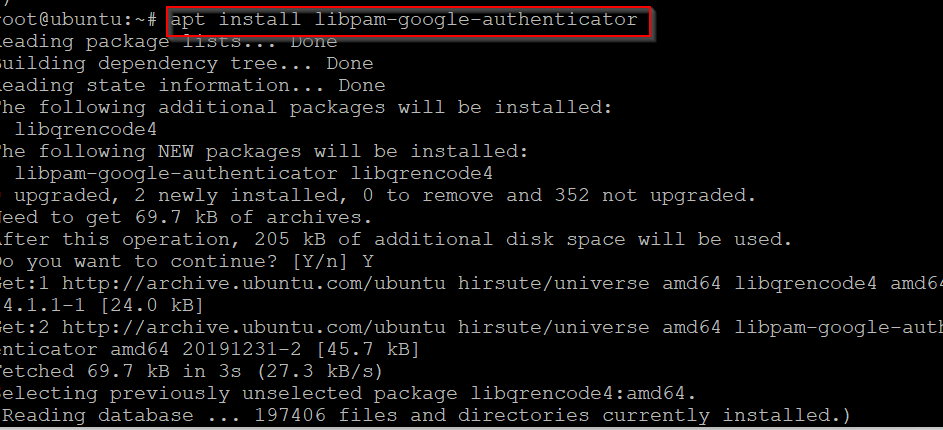
In my case I was not able to install the required package at the first attempt, will be good to run the following command before installing the Package.
# sudo add-apt-repository universe
Then, install google PAM.
# apt install libpam-google-authenticator
Launch application.
# google-authenticator
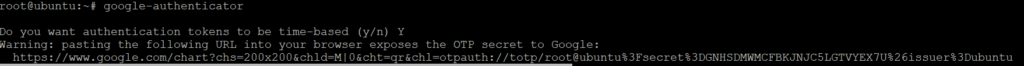
A QR code will appear, scan the code with your Android device.
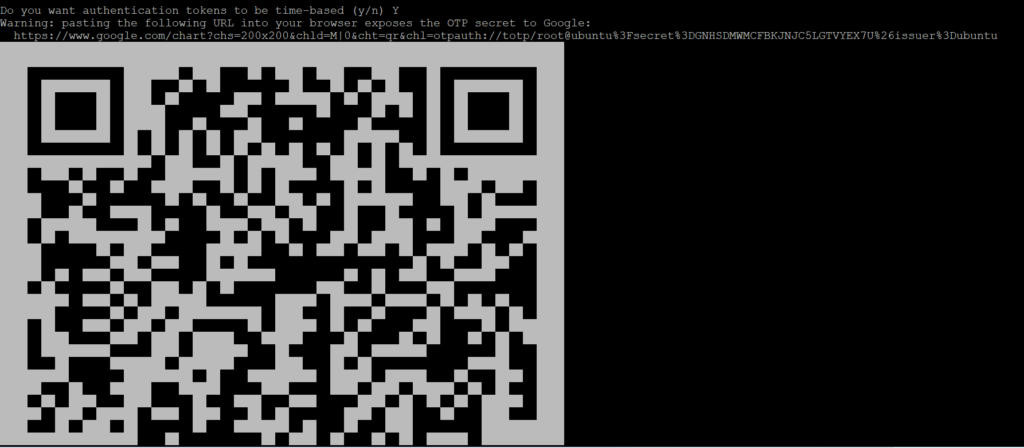
After the device gets paired, a secret code will appear on mobile. Enter those keys here.
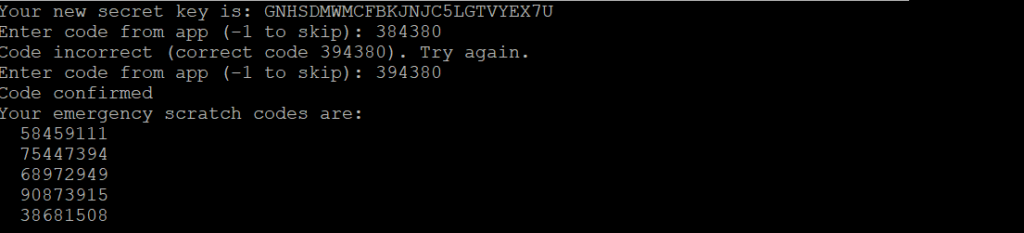
So, press Y
Do you want me to update your "/root/.google_authenticator" file? (y/n) Y
Press Y
In order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. This allows for a time skew of up to 30 seconds between authentication server and client. If you experience problems with poor time synchronization, you can increase the window from its default size of 3 permitted codes (one previous code, the current code, the next code) to 17 permitted codes (the 8 previous codes, the current code, and the 8 next codes). This will permit for a time skew of up to 4 minutes between client and server. Do you want to do so? (y/n) Y
Press Y
If the computer that you are logging into isn't hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting? (y/n) Y
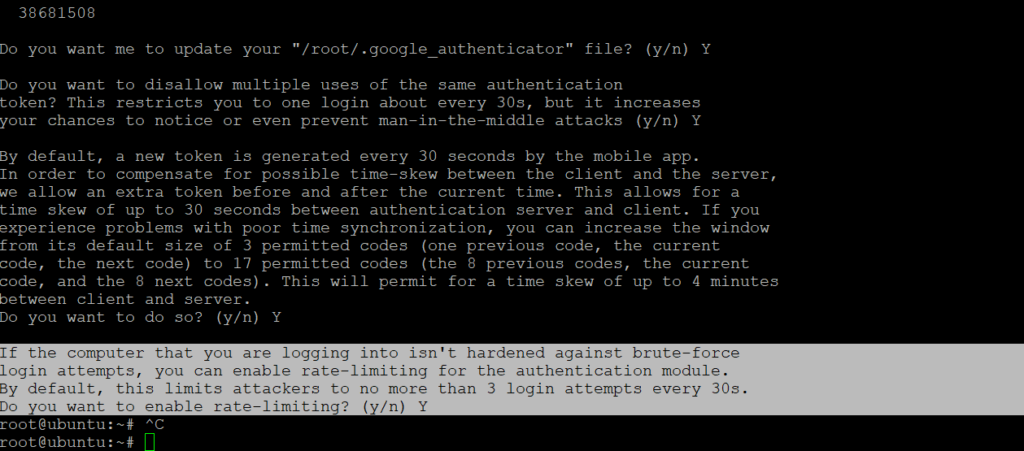
This method can secure devices at max. The secret key will appear on a mobile device for merely 30 seconds. Such a combination is hard to breach any hacker. Such key pairs can guarantee a security layer for the authentication system.
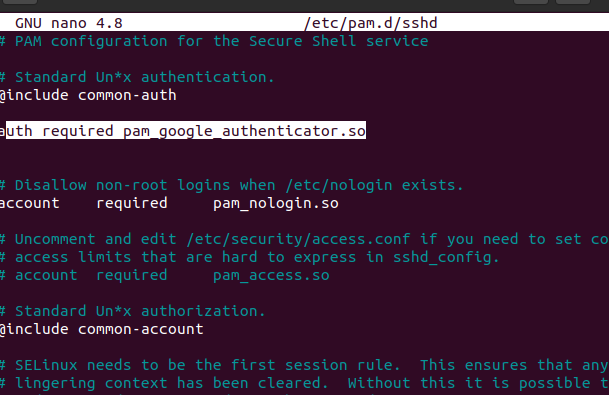
Edit /etc/pam.d/sshd, amend following line.
auth required pam_google_authenticator.so
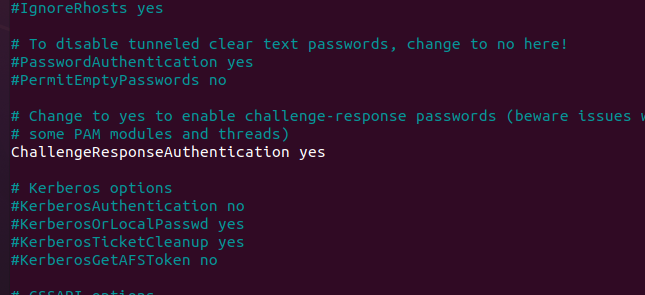
Edit /etc/ssh/sshd_config
Search for ChallengeResponseAuthentication, change from no to yes. Save and Exit.
Finally, Reboot system, now terminal will ask for authentication key, provide from Google authenticator.



