What is Hash Function ?
This is the third and last article in the series Understand Cyber Security and Cryptography. The hash function is used to protect data integrity. Hashing is the process of converting an input of any length into a fixed size of string or text. A message to be based on is called input. The Algorithm used to do so is called has to function. Output is called has value or digest.
Well, how the hash is different from Encryption. Using a key or pair of keys can encrypt or decrypt messages is called encryption. But, the hash is one way you can not generate an original message back from the hash. There must be some quality in the hash function.
- The output must be unique.
- Hash function must be quick to produce the hash value.
- Hash function must be secure.
Some popular applications can be :
- Authenticating a message.
- Storing password.
- Monitoring data integrity.
- Blockchain technology.
Some of the characteristics of Hash Function:
- Application for any size of block of data.
- Strong collision resistence i.e. you can not gerenate same hash value from another block of data.
What is a digital signature?
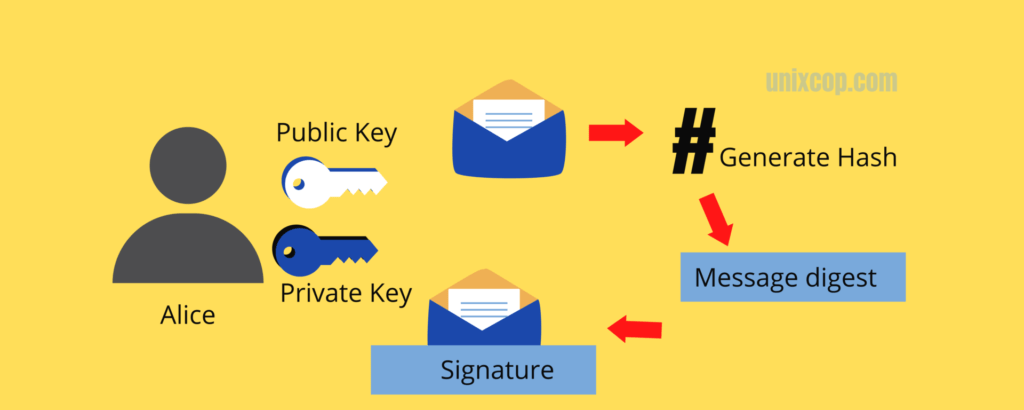
One way cryptography is the crucial part of Cyber Security and Cryptography. Bob has two keys as private and public. The content of Bob’s message is sent through a hash function. After getting through has a hash function output is generated called a digest. that digest is then encrypted with Bob’s private key. Finally, the output will become a digital signature.
A digital signature is a complication of a document and the author’s private key. Any change in the content of the document or private key will create a different signature. Alice can always generate a hash value, if it doesn’t look the same the document is tempered.
What is a PKI or Public Key Infrastructure?
When we are sharing entities over the internet while dealing with public keys trust factor can be an issue. There are two ways of trust- the web of trust and certificates. PKI can resolve that concern. PKI is a framework used to provide trust. It uses a trusted third-party authority by authenticating entities/digital signatures. The certificate authority is responsible for issuing, revoking, and distributing digital certificated. Verisign, GoDaddy, and Thawte are examples of PKI providers.
What is X.509?
It is a standard for defining digital certification. PKI uses an X.509 certificate from the Certificate Authority like GoDaddy to provide assurance that a public key belongs to a specific entity.
Understanding password
Passwords are the most targeted aspects. A lot of methods are used to keep passwords secured. When a user creates a password it did not get stored in the database as such. Password has to go through a hash method and that generated value is stored. Every time user longs with the same password, the hash value will be similar.
Why password is stored using hashing instead of cryptography? the reason is if some have the key can have access to all password database. This is not possible with Hahsing due to one-way encryption.
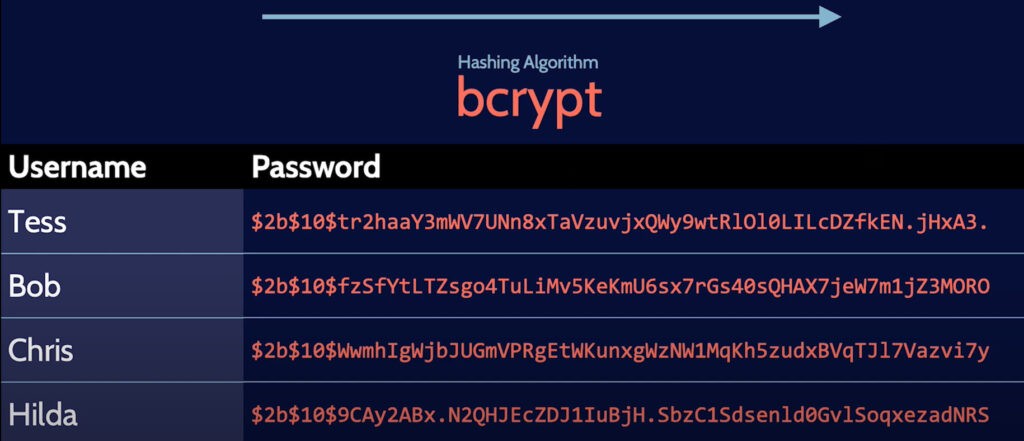
Password can further be protected using the salting method. Salt is a randomly generated value that is added before each has value. Salt is not secret, they are simply amended to the password before hashing. The system does salting by itself and the user is not aware of it. Stay tuned, in the future we will come up with a more interesting series based on Cyber Security and Cryptography.