Introduction
So, in previous RHEL releases, the authconfig command was used to control the authentication of user logins on local and remote systems. Authentication methods and various authentication configurations using each of this tool. The authconfig command became too complex as a central management tool and troubleshoot problems with authentication setup. Moreover, for authselect, sssd, steps are indicated below tutorial. Red hat documentation on this link. Configuring Openldap for sssd service.
So, The authselect utility consists of the components:
- authselect command to manage system authentication. So, you need to be the root user to run this command.
- Three ready-made profiles implement specific types of authentication. So, /usr/share/autoselect/is the default directory: for the profiles
- sssd profile. This profile uses the sssd service to perform system authentication. This profile is automatically selected by default after an RHEL 8 installation.
- winbind profile. This profile uses the winbind service to perform system authentication.
- The nis profile is included in the directory to maintain compatibility with legacy configurations.
Profiles and Supported Features for authselect sssd
| Feature Name | Description |
|---|---|
with-faillock | Lock the account after too many authentication failures. |
with-mkhomedir | Create home directory on user’s first log in. |
with-ecryptfs | This, enable automatic per-user ecryptfs. |
with-smartcard | Authenticate smart cards through SSSD. |
with-smartcard-lock-on-removal | Lock the screen when the smart card is removed. Requires that with-smartcard is also enabled. |
with-smartcard-required | Only smart card authentication is operative; others, including password, are disabled. Requires that with-smartcard is also enabled. |
with-fingerprint | Authenticate through fingerprint reader. |
with-silent-lastlog | Disable generation of pam_lostlog messages during login |
with-sudo | Enable sudo to use SSSD for rules besides /etc/sudoers. |
with-pamaccess | Refer to /etc/access.conf for account authorization. |
without-nullock | Do not add the nullock parameter to pam_unix |
As a default profile, authselect sssd features are automatically enabled.
# sudo authselect current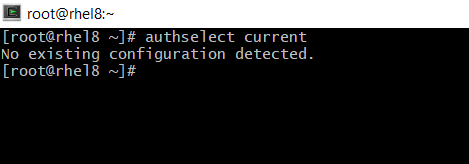
So, We haven’t setup a profile yet. The output should be “No existing configuration detected.”
Creating authselect profile
The following example shows how you would add additional functionalities to the default sssd profile.
First, creating Custom Profiles:
So, If you do not want to use the ready-made profiles from RHEL 8 or vendor-provided profiles, you can create your own specific profile. Follow these steps:
# sudo authselect create-profile newprofile -b sssd \
--symlink-meta --symlink-pam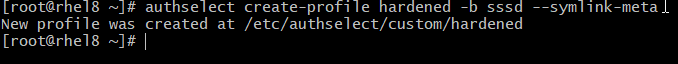
Then, select your custom profile.
# authselect select custom/hardened --force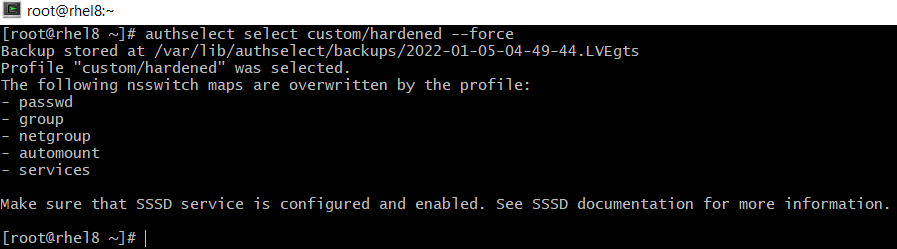
Then, verify the configuration of the custom profile.
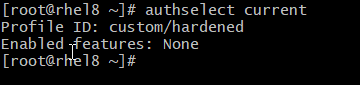
| Options | Description |
| newprofile | Name of your custom profile. |
| template | Base to be used for the custom profile, which is either sssd or winbind. |
| –symlink-meta | Creates symbolic links to the meta files in the original directory of the template profile you are using as base. |
| –symlink-pam | Creates symbolic links to the PAM templates in the original directory of the template profile you are using as base. |
So, this command creates an /etc/authselect/custom/newprofile directory that contains the
symbolic links to the files in the base’s original directory.
So, Automatically lock an account after too many authentication failures (with-faillock):
# sudo authselect requirements sssd with-faillock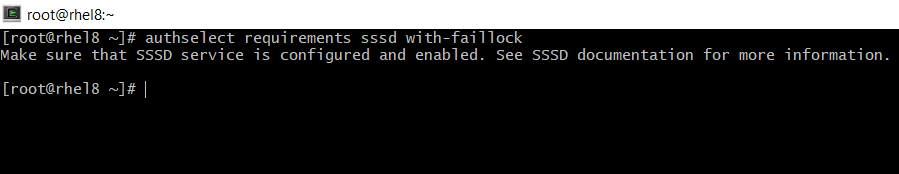
Then, Automatically create a user home directory at the user’s first time log in (with-mkhomedir).
# sudo authselect requirements sssd with-mkhomedir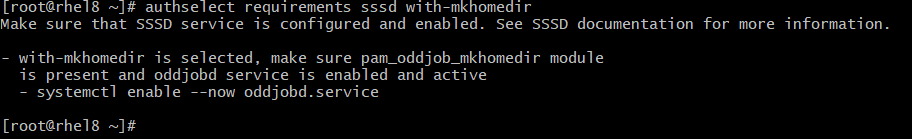
After that, enable both profile features:
# sudo authselect enable-feature with-faillock# sudo authselect enable-feature with-mkhomedirThen, confirm that both profile features have been enabled:
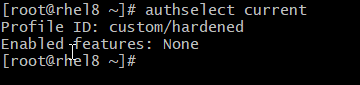
After that, apply the changes.
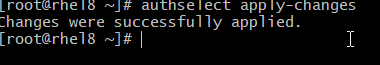
# authselect apply-changes