Hello, friends. Getting network statistics is a basic task that allows you to monitor what is going on with your network. So, today, you will learn how to use the tcpdump command on Linux. We will also use examples to facilitate the tutorial.
Introduction
According to the project website
TCPDump is a powerful command-line packet analyzer; and libpcap, a portable C/C++ library for network traffic capture.
One of the advantages of this tool is that you can install it on many operating systems. Thus, some of the most supported ones are:
- GNU/Linux
- macOS
- NetBSD
- OpenBSD
- OpenWrt
As you can see, there are desktop systems but also at server and router level like OpenWRT.
Install TCPDump on Linux
Normally, this tool is already installed by default on Linux. However, it is better to be sure
In the case of Debian, Ubuntu and derivatives run in terminal
sudo apt install tcpdumpFor RHEL and family members
sudo dnf install tcpdumpThis is also true for all other Linux distributions. It is very likely that tcpdump is in their official repositories.
Examples of how to use the tcpdump command on Linux
TCPDump is so powerful that there are multiple usage options. However, I will summarize some common and useful ones for most users that exist.
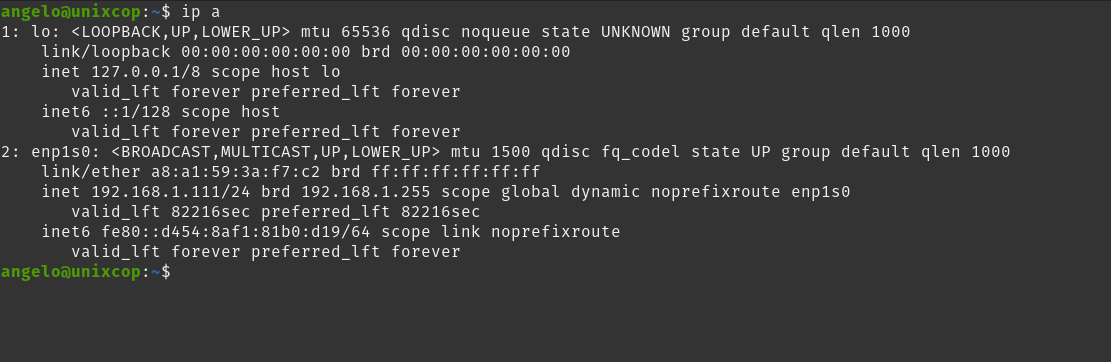
For this post, it is assumed that the name of the network interface to be examined is enp1s0 but if you want to be certain which one is yours run
ip aIt will show you something similar to this.
Show everything on an interface
If you would like to show all the necessary information about an interface, then you can use
sudo tcpdump -i [interface]You will get an output screen like this
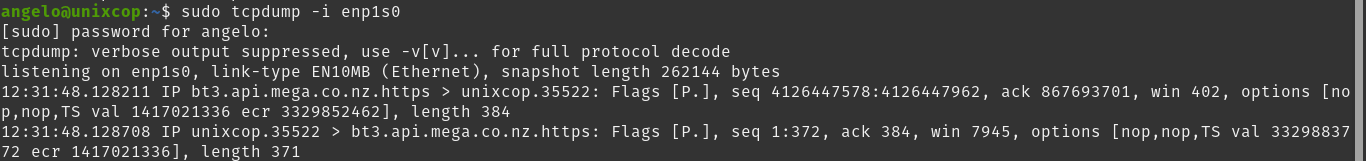
But you can also use any to get information about all of them, even if it is not so clear
sudo tcpdump -i anyOf course, you can also specify a specific port
sudo tcpdump -i [interface] port [port]Capture a specified number of packets
The above command does not capture packets until you press CTRL + C but you can specify a few packets.
sudo tcpdump -c 4 -i [interface]In this case, only 4 packets will be captured for the given interface. This helps to filter the information a bit.
Find Traffic by IP
You can also further filter traffic by IP address. To do this run.
sudo tcpdump host [IP]Filter packets by destination or by source
This option is useful for monitoring activity on an IP address as either a destination or source.
sudo tcpdump src [IP]
sudo tcpdump dst [IP]Filter by protocol
Although TCP is the most commonly used protocol, some tools also use UDP. If you’d like, you can filter this traffic by protocol.
sudo tcpdump -n udpDisplay all available interfaces
Although there are many ways to do this that include other programs, with TCPDump it is as simple as running
sudo tcpdump -DSample Output:
1.enp1s0 [Up, Running, Connected]
2.any (Pseudo-device that captures on all interfaces) [Up, Running]
3.lo [Up, Running, Loopback]
4.bluetooth0 (Bluetooth adapter number 0) [Wireless, Association status unknown]
5.bluetooth-monitor (Bluetooth Linux Monitor) [Wireless]
6.nflog (Linux netfilter log (NFLOG) interface) [none]
7.nfqueue (Linux netfilter queue (NFQUEUE) interface) [none]
8.dbus-system (D-Bus system bus) [none]
9.dbus-session (D-Bus session bus) [none]Export the results to a file
The most convenient way is to save the results in a file that can be processed by other programs. Of course, TCPDump can also do this.
sudo tcpdump port 80 -w file.pcapIn this case, all packets are inspected on port 80 but this is just an example. Then with the -w option followed by the name (can be the path as well) you write the results to it.
Read the results from a file
Once you have the file ready, you can use it for your analysis. This can be done by tcpdump or another similar tool.
sudo tcpdump -r file.pcapConclusion
In this post, you got the basics of using TCPDump, and it is a very effective and invaluable tool.



