This post is about Suricata Network IDS integration with WAZUH.
Wazuh is an excellent HIDS (Host-based Intrusion Detection System) among other things. In addition to it’s rule-based analysis of log events from agents and other devices, it also performs file integrity monitoring and anomaly detection. This provides a great deal of insight into the security of your digital assets. However, some security issues are most successfully detected by inspecting a server’s actual network traffic, which generally is not accounted for in logs. This is where a NIDS (Network Intrusion Detection System) can provide additional insight into your security in a way that is highly complimentary to the HIDS functionality in Wazuh.
Suricata is one such NIDS solution, which is open source and can be quickly deployed either on dedicated hardware for monitoring one or more transit points on your network, or directly on existing Unix-like hosts to monitor just their own network traffic. Because Suricata is capable of generating JSON logs of NIDS events, it integrates beautifully with Wazuh.
Suricata Network IDS integration with WAZUH
Configure your environment as follows to test the POC.
- Install Suricata (tested with version 5.0.7) on the CentOS 8 monitored endpoint. This requires EPEL repository that depends on your operating system version.
yum install https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm
yum -y install suricata-5.0.7Download and extract Emerging rules.
cd /tmp/
curl -LO https://rules.emergingthreats.net/open/suricata-5.0.7/emerging.rules.tar.gz
tar -xvzf emerging.rules.tar.gz && mv rules/*.rules /etc/suricata/rules/
chown suricata:suricata /etc/suricata/rules/*.rules
chmod 640 /etc/suricata/rules/*.rulesModify Suricata settings in the /etc/suricata/suricata.yaml file.
EXTERNAL_NET: "any"
default-rule-path: /etc/suricata/rules
rule-files:
- "*.rules"Start Suricata.
systemctl enable suricata
systemctl daemon-reload
systemctl start suricataConfigure the Wazuh agent to read Suricata logs file. The following settings need to be added to the /var/ossec/etc/ossec.conf file of the monitored CentOS 8 endpoint.
<localfile>
<log_format>syslog</log_format>
<location>/var/log/suricata/eve.json</location>
</localfile>Restart the Wazuh agent to apply the changes.
systemctl restart wazuh-agentSteps to generate the alerts
No action is required. Wazuh automatically parses data from /var/log/suricata/eve.json and generates related alerts.
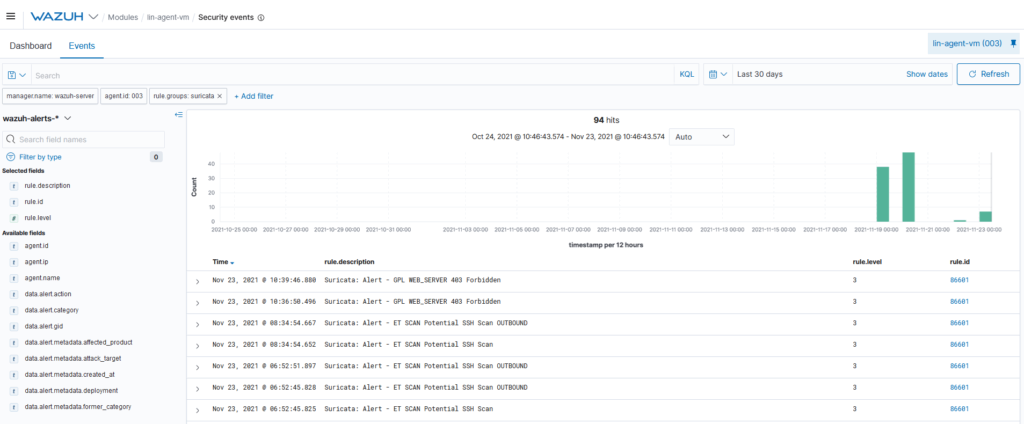
You can visualize the alert data in the Wazuh Kibana plugin. To do this, go to the Security events module and add the filters in the search bar to query the alerts.
Troubleshooting
- Error concerning network interface in Suricata log file
/var/log/suricata/suricata.log.
To solve this issue, check the name of your network interface and configure it accordingly in the files /etc/sysconfig/suricata and /etc/suricata/suricata.yaml.
That’s all for Suricata Network IDS integration with WAZUH.



