Introduction
You can SSH to your Linux instance as root with the key. However, the key doesn’t work for non-root users.
So we will illustrate two methods to use SSH keys with non-root users.
Method 1: Create a New SSH Key
Just follow the steps below
- SSH to your Linux instance as a root
- Create an SSH key for a user
sudo -u ssh_user ssh-keygenFor example
sudo -u unixcop ssh-keygen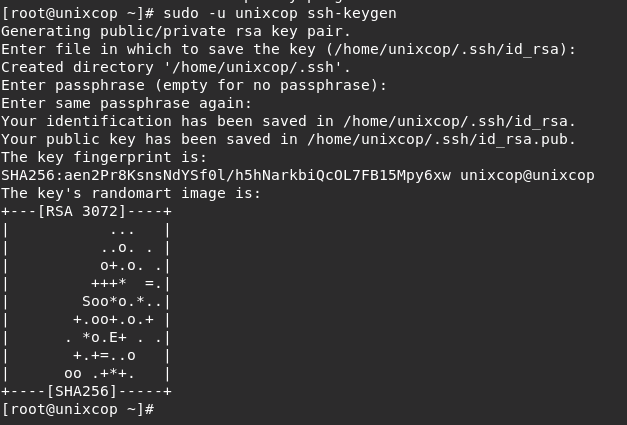
- Then save the private key, /home/ssh_user/.ssh/id_rsa , to your computer.
For example:
Copy it to your local .ssh folder as ~/.ssh/ssh_user_id_rsa
- Delete the private key from your Linux instance with the below command.
rm /home/ssh_user/.ssh/id_rsa- Rename the public key to authorized_keys.
mv /home/ssh_user/.ssh/id_rsa.pub /home/ssh_user/.ssh/authorized_keysNOTE: If you saved the private key as ~/.ssh/ssh_user_id_rsa, you can SSH to the server as your non-root user.
ssh -i ~/.ssh/ssh_user_id_rsa [email protected]Method 2: Move the root SSH Key to the Non-root User
Here, We will move the root key to the ssh_user, which also disables the root user’s SSH key access.
So just follow the steps below:
- SSH to Linux instance as root.
- Create the .ssh directory for ssh_user.
mkdir /home/ssh_user/.ssh- Move the root key to ssh_user’s SSH directory.
mv /root/.ssh/authorized_keys /home/ssh_user/.ssh/- Change the ownership of the .ssh directory from root to ssh_user so OpenSSH can read.
chown -R ssh_user:ssh_user /home/ssh_user/.sshConclusion
In this short tutorial, We explained two methods to use SSH keys with non-root users.
Thank you!!



