Following is the procedure of installation of fdroid server. Run all commands with debian user, use sudo where necessary
F-DROID INSTALLATION
apt-get install software-properties-common
add-apt-repository "http://deb.debian.org/debian buster-backports main"
apt update
apt-get install fdroidserver/buster-backports
mkdir ~/android-sdk-linux
cd ~/android-sdk-linux
wget https://dl.google.com/android/repository/commandlinetools-linux-6858069_latest.zip
echo "87f6dcf41d4e642e37ba03cb2e387a542aa0bd73cb689a9e7152aad40a6e7a08 commandlinetools-linux-6858069_latest.zip" | sha256sum -c
commandlinetools-linux-6858069_latest.zip: OK
unzip commandlinetools-linux-6858069_latest.zip
export ANDROID_HOME="$HOME/android-sdk-linux"
./cmdline-tools/bin/sdkmanager --sdk_root="$ANDROID_HOME" platform-tools "build-tools;30.0.3"
echo export ANDROID_HOME=$ANDROID_HOME >> .bashrc
F-DROID REPO CONFIGURATION WITH NGINX
sudo apt-get install nginx
sudo mkdir /usr/share/nginx/www
sudo mkdir /usr/share/nginx/www/fdroid
sudo chown -R $USER /usr/share/nginx/www/fdroid
cd /usr/share/nginx/www/fdroid
fdroid init
nano /etc/nginx/sites-enabled/default
(Do the following):
changed the root directory by adding following line:
root /usr/share/nginx/www;
Delete or comment /var/www/html
sudo service ngnix restart
cd /usr/share/nginx/www/fdroid
Now place your apk files in repo directory
cp /path/to/*.apk /usr/share/nginx/www/fdroid/repo/
fdroid update --create-metadata
fdroid update
adduser android
Password set: android
nano /usr/share/nginx/www/fdroid/config.yml
(add following line)
serverwebroot: android@localhost:/usr/share/nginx/www/fdroid
I2P INSTALLATION AND CONFIGURATION STEPS (INCLUDING IPTABLES RULES & I2P AS SYSTEM SERVICE)
I2P INSTALLATION:
sudo apt-get update
sudo apt-get install apt-transport-https curl
sudo apt-get install i2p
IPTABLES CONFIGURATION FOR I2P:
iptables -I INPUT -p tcp -m tcp --dport 7657 -j ACCEPT
iptables -I INPUT -p tcp -m tcp --dport 7658 -j ACCEPT
vi /etc/sysctl.conf
(Add following line at bottom of sysctl.conf)
net.ipv4.conf.eth0.route_localnet=1
(Save and exit)
(Run Following commands):
sysctl –p
iptables -t nat -I PREROUTING -p tcp -d 0.0.0.0/0 --dport 7657 -j DNAT --to-destination 127.0.0.1:7657
iptables -t nat -I PREROUTING -p tcp -d 0.0.0.0/0 --dport 7658 -j DNAT --to-destination 127.0.0.1:7658
iptables-save > /etc/iptables.rules
crontab -e
@reboot sudo iptables-restore -n </etc/iptables.rules
SET I2P SERVICE TO START AT REBOOT:
systemctl enable i2p
systemctl start i2p
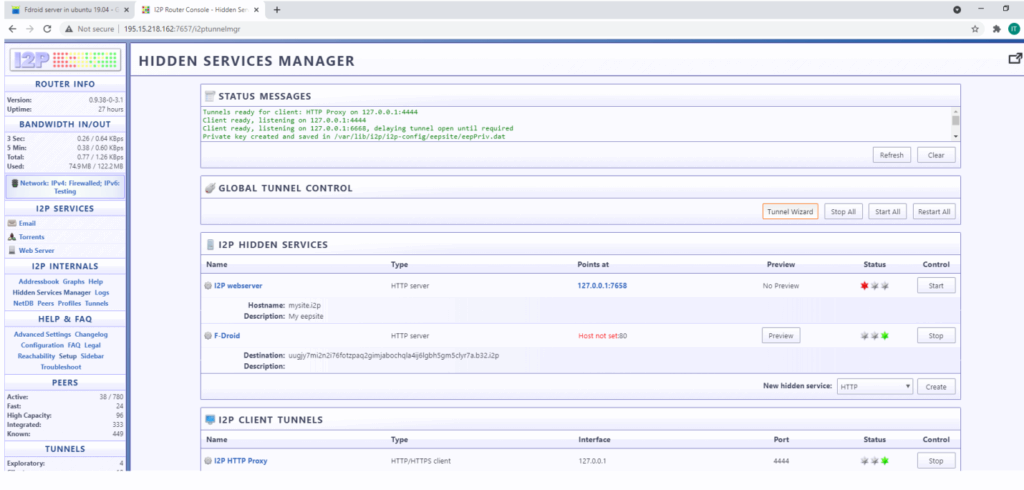
Access in browser http://195.15.218.162:7657/config and click on Hidden Service Manager
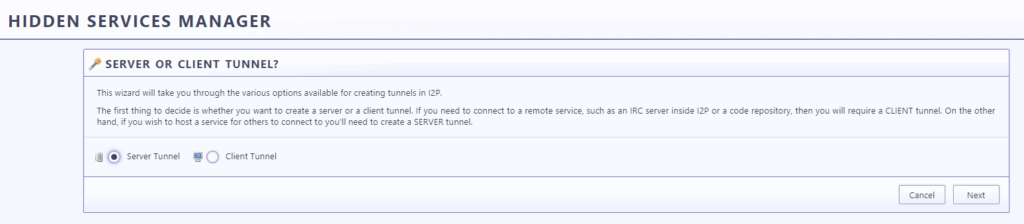
Click on Tunnel Wizard
Select Server Tunnel and click on next
Select the Tunnel HTTP and click on next
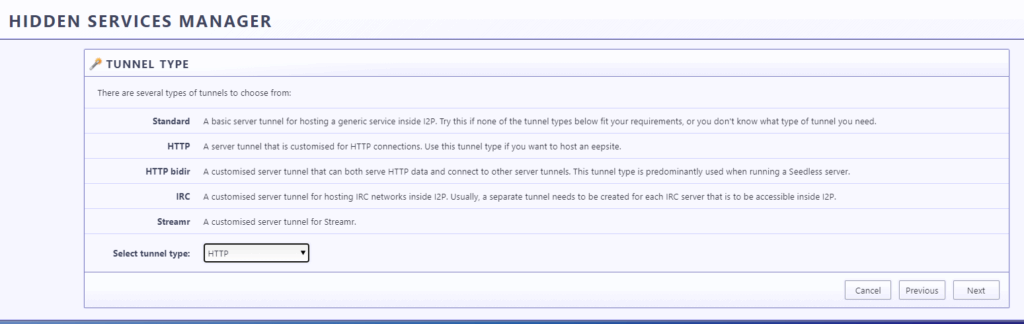
Type the any tunnel name in our case “F-DROID”
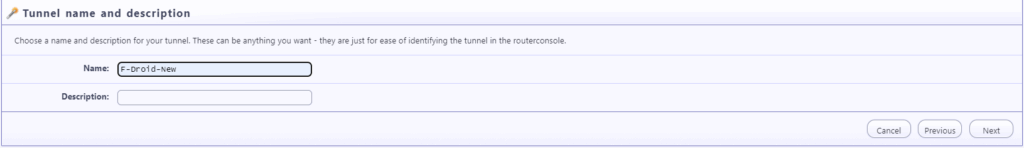
Type Host: 127.0.0.1, port: 80
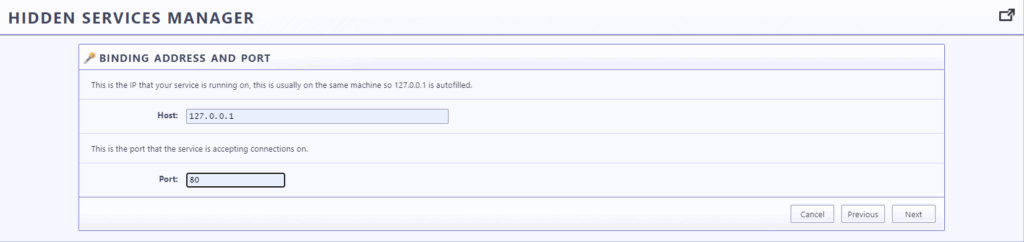
Put check on Automatically start tunnel when router starts and Click on Finish
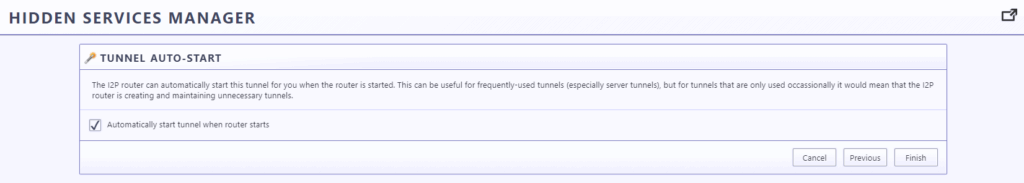
Now tunnel will be available as shown in below picture, and i2p link is available with F-Droid tunnel as Destination: nkymfwaye5okwsygtihhghvn5ocsxau6ln6dayjmc5rieabeuooq.b32.i2p
Accessible as:
http://nkymfwaye5okwsygtihhghvn5ocsxau6ln6dayjmc5rieabeuooq.b32.i2p/fdroid/repo
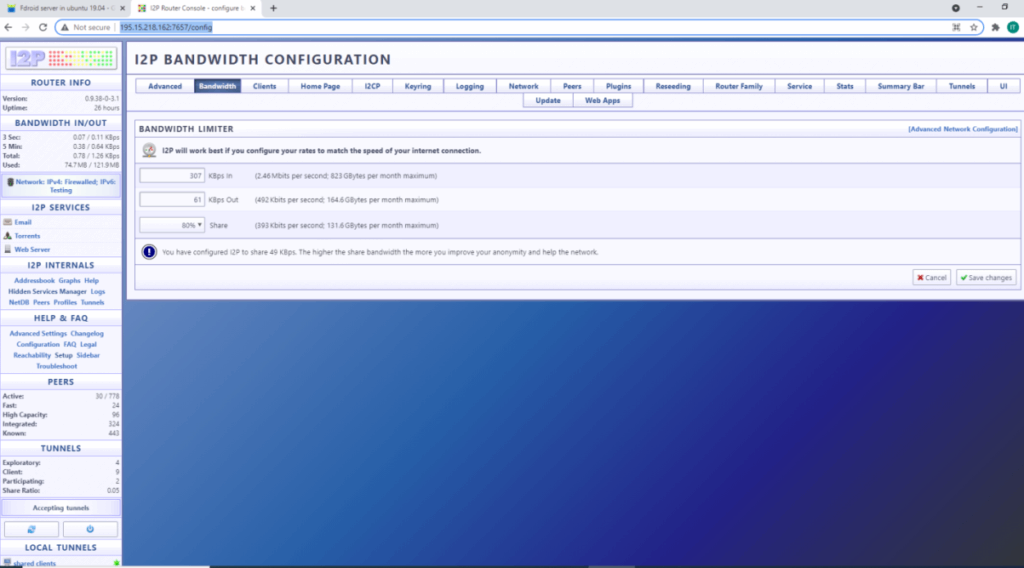
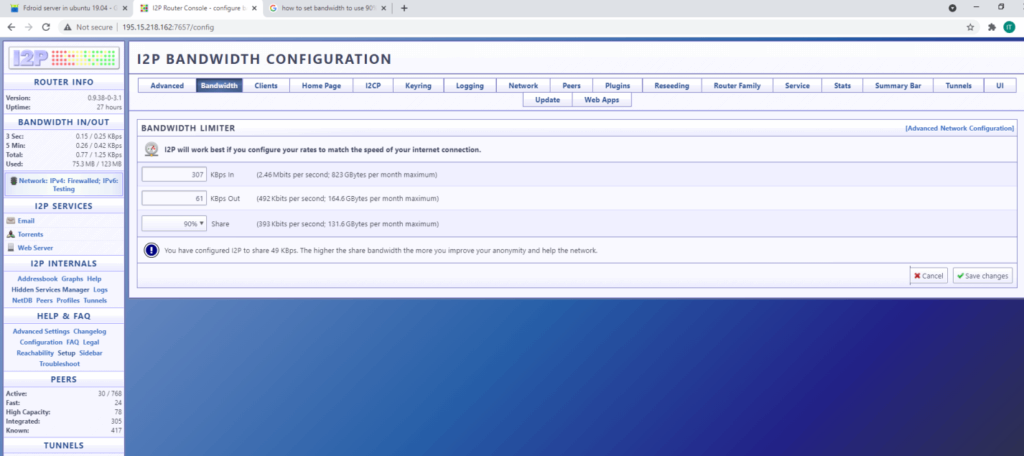
CONFIGURE I2P TO USE 90% OF THE BANDWIDTH
Access in browser http://195.15.218.162:7657/config and click on Bandwidth and select 90% as shown below
NGINX CONFIGURATION FOR I2P
As we have already set iptables during installation of I2P, now just we have to do following configuration in nginx.
cd /etc/nginx/sites-enabled
nano default
comment out “listen 80 default_server;” and ”listen [::]:80 default_server;” and add following lines
listen 127.0.0.1:80;
server_name 127.0.0.1;
Save and exit and then restart nginx service as follows
systemctl restart nginx
ACCESS METHOD OF F-DROID REPOSITORY USING I2P URL
STEP 1:
Download and install F-Droid.apk on your mobile from following link
https://f-droid.org/F-Droid.apk
STEP 2:
Since we are using I2P url, to access i2p URL will have to install invizible pro app from google store:
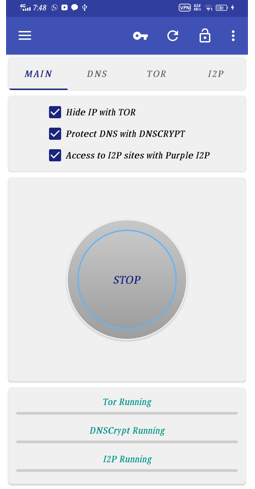
Open invizible pro app, check on all 3 check boxes and click on start
STEP 3:
Now open F-droid app installed in STEP 1, and go to settings as show below
Now click on repositories and turn off all if any repo is open
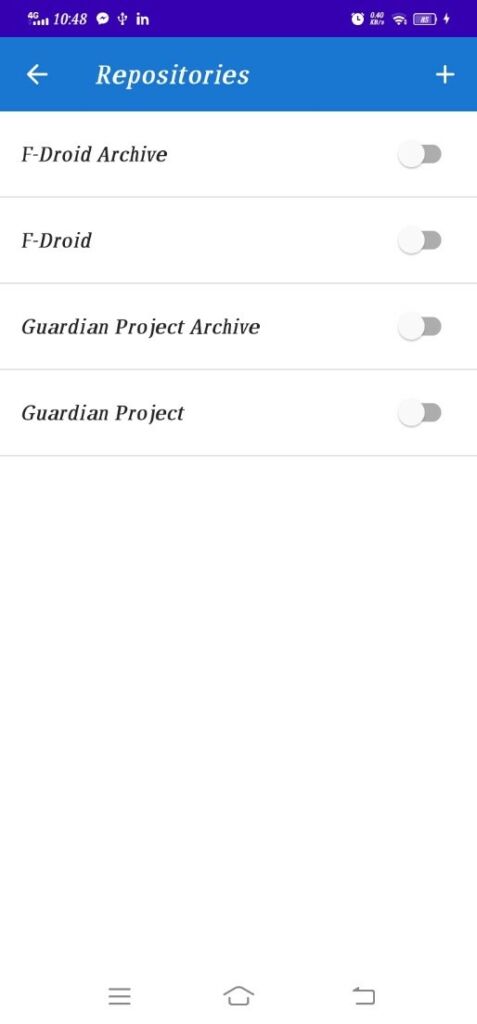
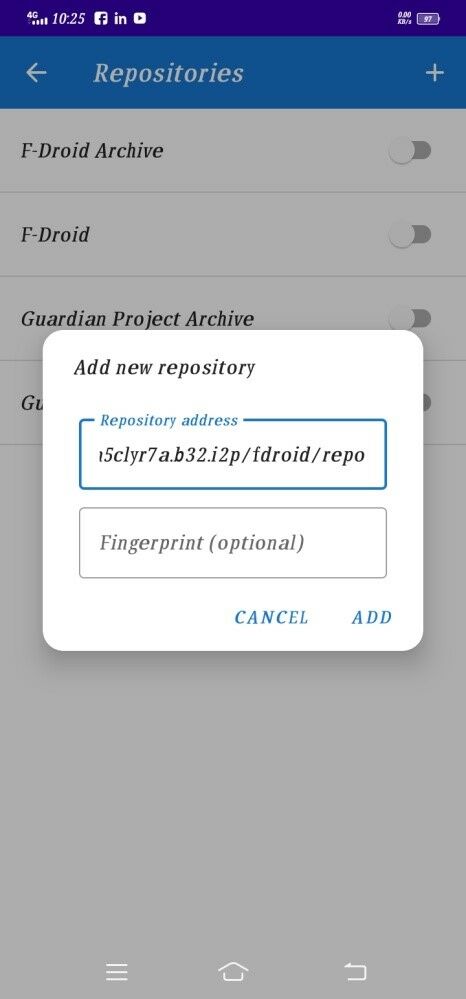
Now click on + sign to add your own repositories
In repositories address enter following address I2P Address
http://nkymfwaye5okwsygtihhghvn5ocsxau6ln6dayjmc5rieabeuooq.b32.i2p/fdroid/repo
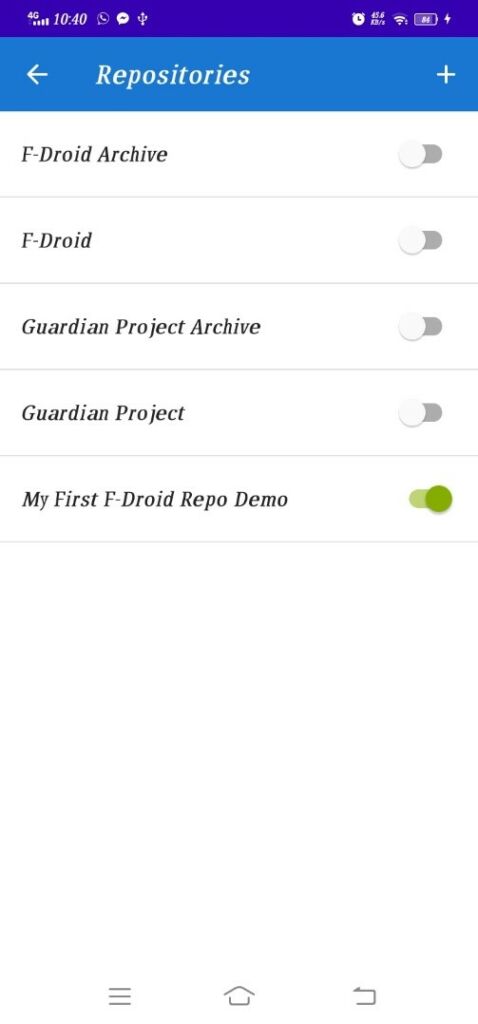
Turn on newly added repository, it will take sometime to sync
We are done, we can download our APKs and install in our Android devices.
PROCEDURE OF UPLOADING AND UPDATING APK FILES TO F-DROID REPO
Download your APKs on your local system
Connect to Server using WinSCP as shown below
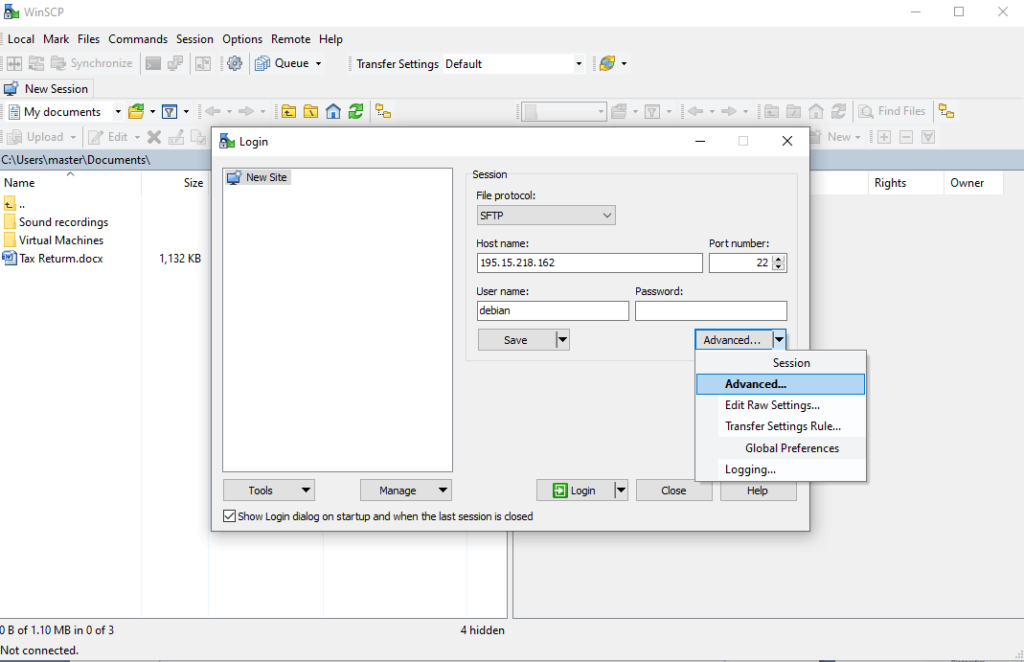
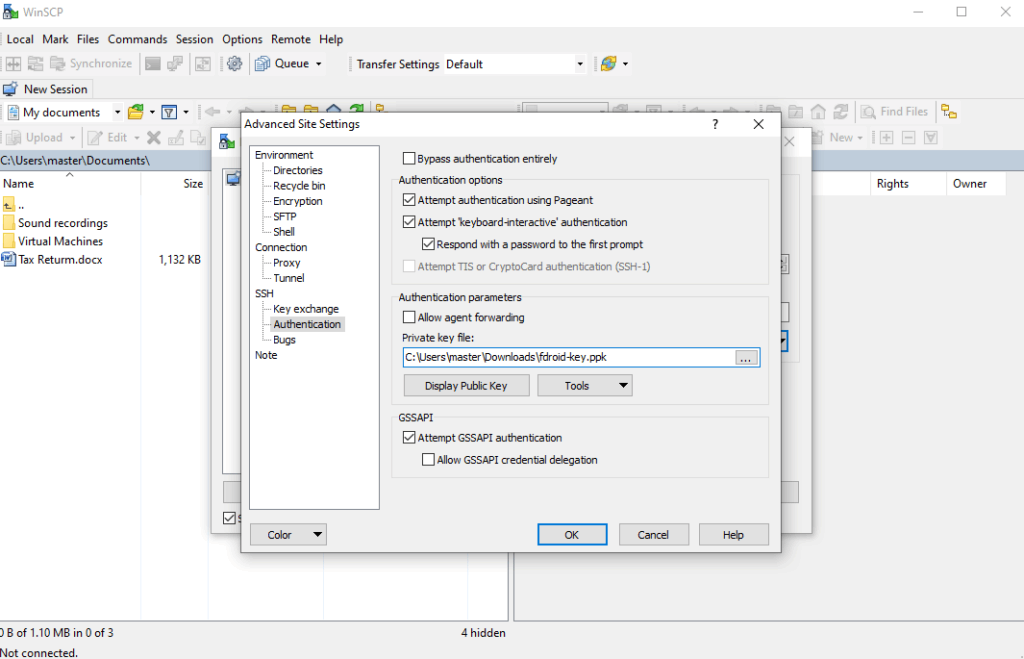
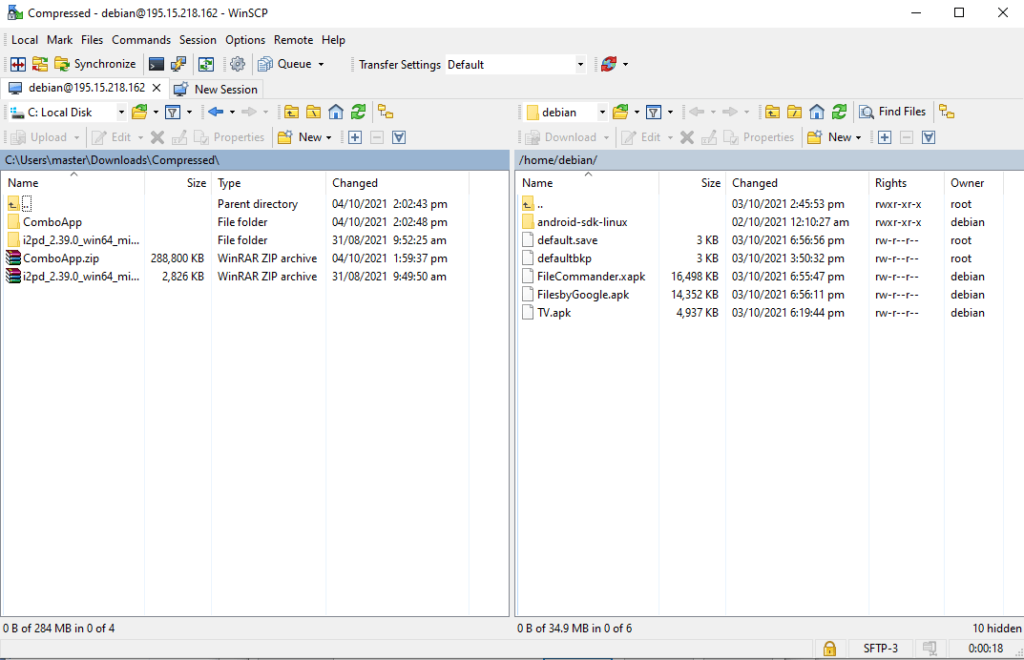
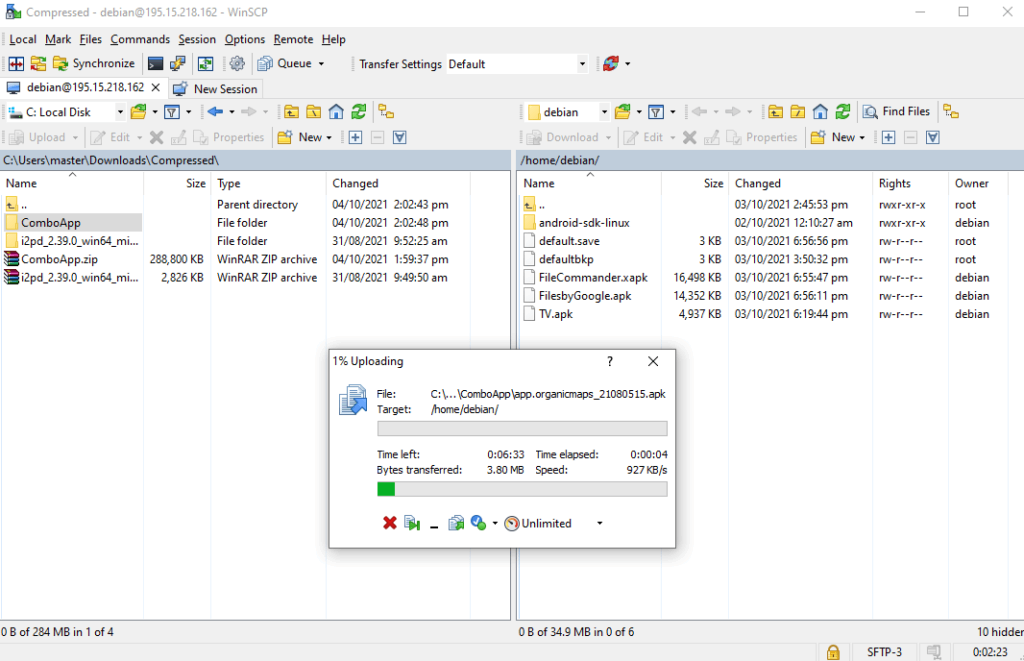
Drag and drop ComboApp (Applications Folder(s)) to debian home directory
Now access the F-Droid server shell using SSH with debian user as you normally do and run following commands
cd /usr/share/nginx/www/fdroid
cp ~/ComboApp/*.apk repo/
sudo fdroid update –c
sudo fdroid update
That’s it. Now open F-Droid client app on your android device and all of the apps you uploaded/updated should be shown there.
CONFIGURE SSH AND SECURE IT TO ACCEPT THE FDROID DEPLOY -V COMMAND
nano /etc/ssh/sshd_config
(Add following line at the end of sshd_config, so android user will not be able to ssh from any remote location)
AllowUsers [email protected] debian
(save and exit)
service sshd restart
fdroid deploy –v
CONFIGURE THE USUAL FAIL2BAN SYSTEM SECURITY TO PROTECT THE SERVER
apt install fail2ban -y
vi /etc/fail2ban/jail.d/jail-debian.local
[sshd]
port = 22
maxretry = 3
service fail2ban restart
CONFIGURE AUTOMATIC SECURITY UPDATES
sudo apt install unattended-upgradesnano /etc/apt/apt.conf.d/50unattended-upgrades
(Uncomment following lines by removing forward slashes)
"origin=Debian,codename=${distro_codename}-updates";
"origin=Debian,codename=${distro_codename},label=Debian";
"origin=Debian,codename=${distro_codename},label=Debian-Security";
SET I2P HOSTNAME FDROID.DEV.I2P
vi /etc/hostname
(replace existing hostname with following)
fdroid.dev.i2p
(save and exit)
Nano /etc/hosts
(add following line)
127.0.0.1 fdroid.dev.i2p
RECOMMENDATIONS FOR SECURITY, SERVER MAINTENANCE AND BACKUPS:
Though I have already audited and applied all the security patches/fixes etc and our server is fully secure now but following are some useful recommendations
– Existing private key may be changed at some later stage
– Offsite/Remote backup should be configured for the data/apps etc
– Weekly snapshot of the VPS be taken through hosting provider.
-Backup of any config file needs to be taken before making changes into it like cp abc.conf to abc.conf-backup – Health check of the sever may be performed every 3 to 4 months just to make sure everything is running fine and server is in good health



