What is NTP Server
Network Time Protocol – NTP- is a protocol which runs over port 123 UDP at Transport Layer and allows computers to synchronize time over networks for an accurate time. While time is passing by, computers internal clocks tend to drift which can lead to inconsistent time issues, especially on servers and clients logs files or if you want to replicate servers resources or databases.
What is Ansible
Ansible is an open-source software provisioning, configuration management, and application-deployment tool enabling infrastructure as code.[2] It runs on many Unix-like systems, and can configure both Unix-like systems as well as Microsoft Windows
Why we need to use ansible for installing and configuration of NTP
Assume we have thousands of servers in your environment and you need to install and configure NTP on all these servers so that they can be synced to central NTP servers. Now you can understand, for installing and configuration of NTP client on thousands server will take lots of days and resources. For resolving resource and time issue here will be use configuration management tools – Ansible. Ansible is an agentless configuration and management tools to we will not require to install agents on remote hosts like other competitive tools Puppet & Chef.
For installing & configuring ansible please click on below link. https://unixcop.com/ansible-installation-configuration-on-centos-7-8/
Ansible Architecture
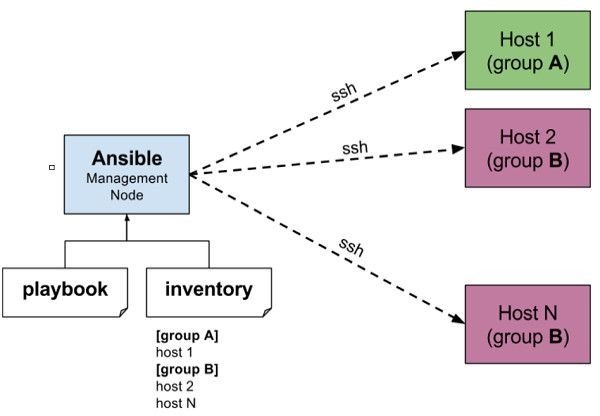
Our Lab setup
Our lab setup is given as below, we have to configure NTP on ntp-client01 & ctp-client02 using ansible playbook.
Ansible Server: 192.168.0.109
NTP Client01: 192.168.0.110
NTP Client02: 192.168.0.112
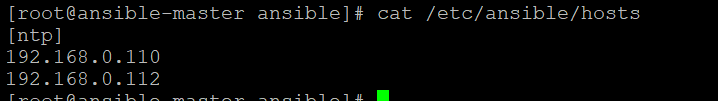
Setup remote hosts in ansible hosts file
To install and configuration NTP on remote hosts Centos machines, we have to add the IP address into the /etc/ansible/hosts files of Ansible server. We have created a group name “ntp” and added our remote hosts IP addresses, we can add many more machines as per our need.
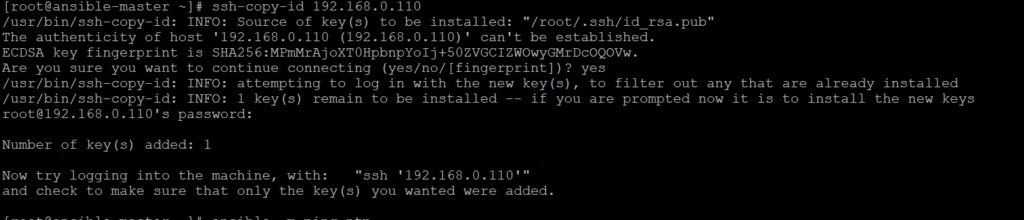
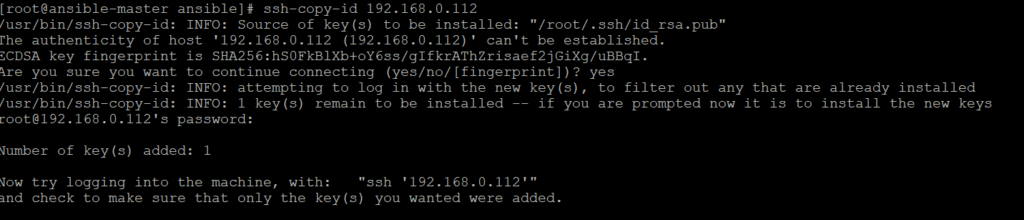
Configuring password less authentication of ansible server with remotes hosts, for this we have to genrate ssh key and copy it on remote hosts
We already have ssh-key available on my ansible server which I will just copy it on 2 remote machines as given below.
Now we can check if our Ansible server is able to communicate with remote servers or not using “ping” module using command “ansible -m ping ntp“
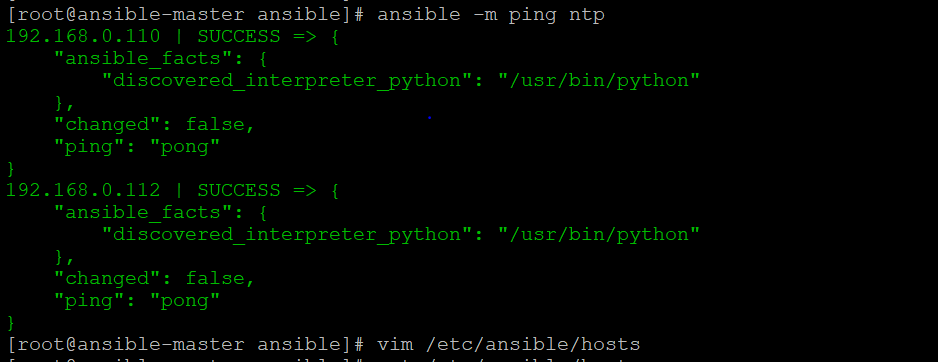
We can see all the hosts in “ntp” group is reachable.
Our ansible setup is ready and we can now install and configure NTP on both remotes hosts in ntp groups using Ansible Playbook.
What is Ansible Playbook ?
Playbooks are the files where Ansible code is written. Playbooks are written in YAML format. YAML stands for Yet Another Markup Language. Playbooks are one of the core features of Ansible and tell Ansible what to execute. They are like a to-do list for Ansible that contains a list of tasks.
Playbooks contain the steps which the user wants to execute on a particular machine. Playbooks are run sequentially. Playbooks are the building blocks for all the use cases of Ansible.
We have written a playbook which will basically allow NTP in firewall, install NTP and configure NT and finally restart NTP services on the remotes hosts.
Lets check if NTP is installed on remotes hosts or not before move forwards
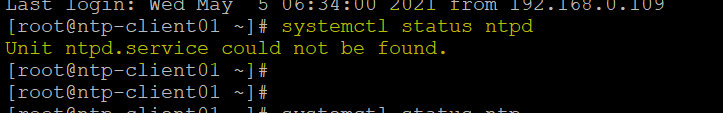
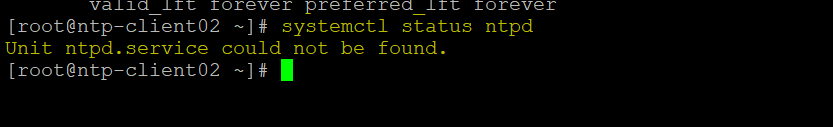
As show in above figures, we can say NTP is not installed on both hosts
Now check if “/etc/ntp.conf” file is available on remote hosts or not
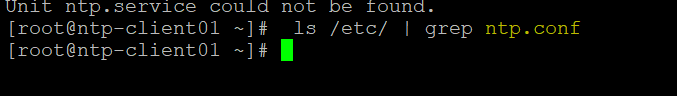
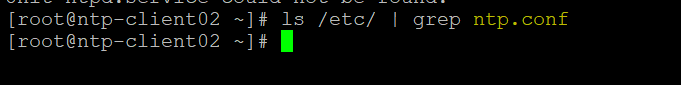
As we can see “/etc/ntp.conf” file is also not available so we can safely move ahead and install and configure NTP on both the machines
For Installing and configuration I have written a playbook that includes tasks which will install, configure, add to firewall list and finally restart services in one go on both servers, below is the Playbook.
# ntp configuration playbook
- hosts: ntp
tasks:
- name: allow ntp through firewall
shell: firewall-cmd --add-service=ntp --permanent
- name: firewall reload
shell: firewall-cmd --reload
- name: Make sure Chrony is started up
service: name=chronyd state=started enabled=yes
tags: chrony
#- hosts: servers
# tasks:
- name: set timezone
shell: timedatectl set-timezone America/New_York
- name: Install NTP
yum: name=ntp state=installed
tags: ntp
- name: Copy over the NTP configuration
# template: src=./template/ntp.j2 dest=/etc/ntp.conf
copy: src=/tmp/ntp.conf dest=/etc/ntp.conf
notify:
- restart ntpd
tags: ntp
- name: Make sure NTP is stopped
service: name=ntpd state=stopped enabled=yes
tags: ntp
- name: Sync time initialy
shell: ntpdate 0.centos.pool.ntp.org
tags: ntp
- name: Make sure NTP is started up
service: name=ntpd state=restarted enabled=yes
tags: ntp
- name: Sync hwclock
shell: hwclock -w
tags: ntp
handlers:
- name: restart ntpd
service: name=ntpd state=restarted
We need ntp.conf file to pass into this playbook, we have saved on our Ansible server in /tmp directory and this will be copied on to both remote hosts.
server 0.centos.pool.ntp.org is the NTP server with which both hosts will be synced.
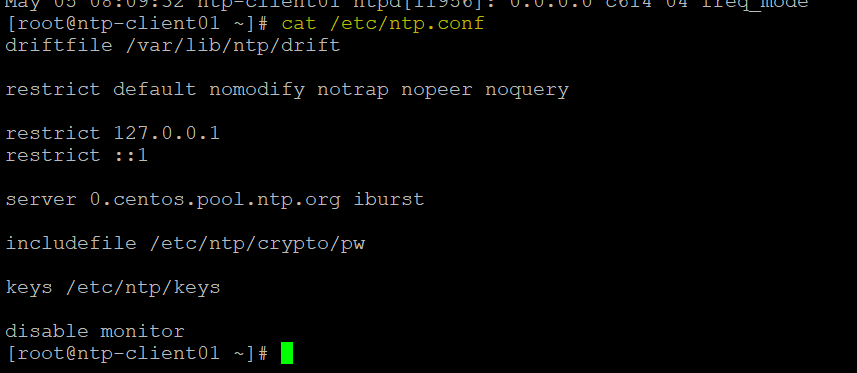
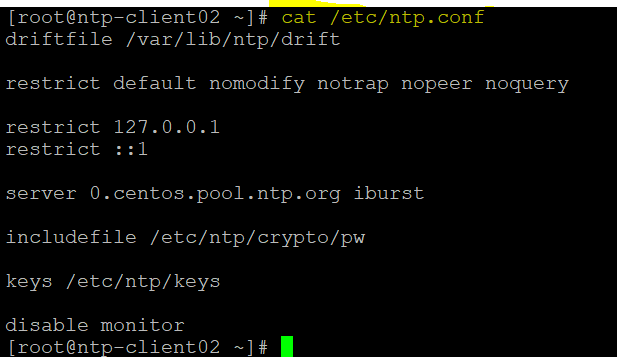
Here is the content of “/tmp/ntp.conf” file
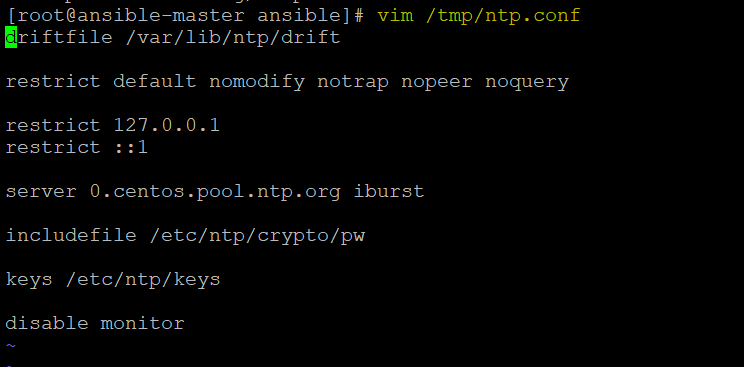
driftfile /var/lib/ntp/drift
restrict default nomodify notrap nopeer noquery
restrict 127.0.0.1
restrict ::1
server 0.centos.pool.ntp.org iburst
includefile /etc/ntp/crypto/pw
keys /etc/ntp/keys
disable monitor
Now we are ready to run the playbook to configure NTP on both servers.
Type command ansible-playbook ntp-configuration.yml to run the playbook, it will hardly take 10-15 seconds to run the playbook. Once it is successfully run you will be able to see something as below
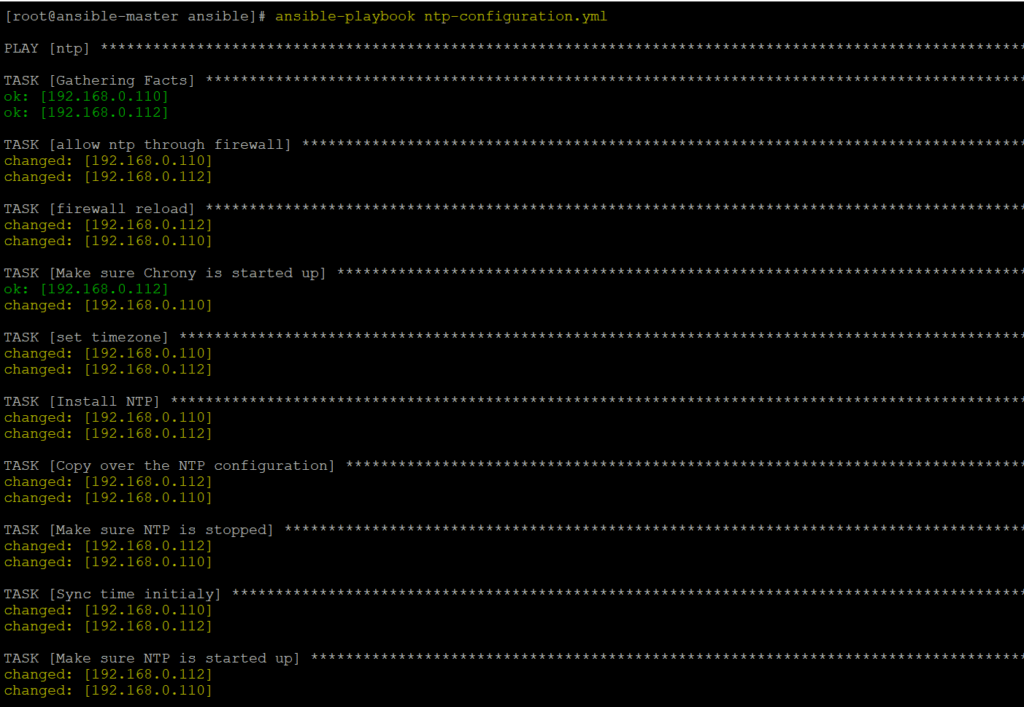
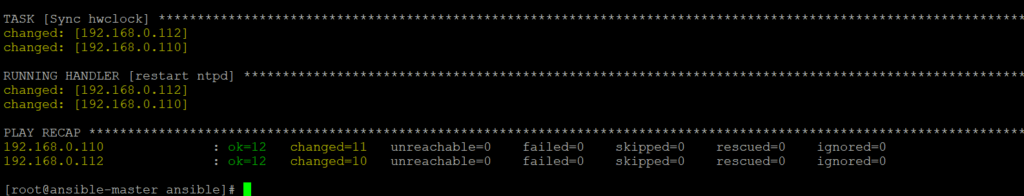
We can now verify NTP is installed on remote hosts or not. We can see NTP service is available with was not there before running playbook
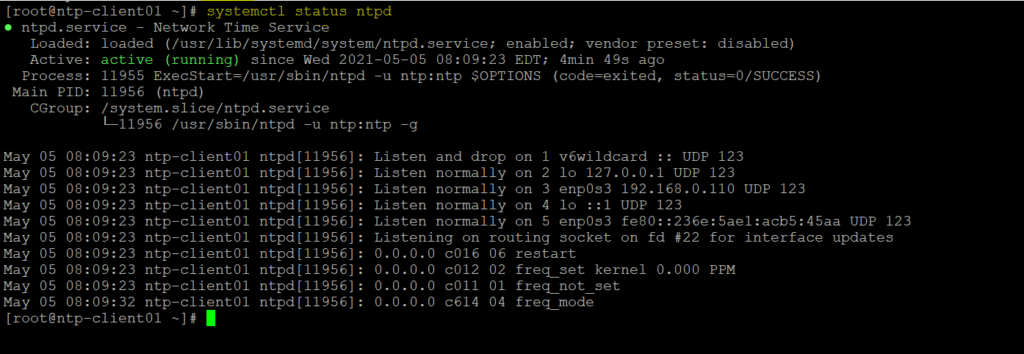
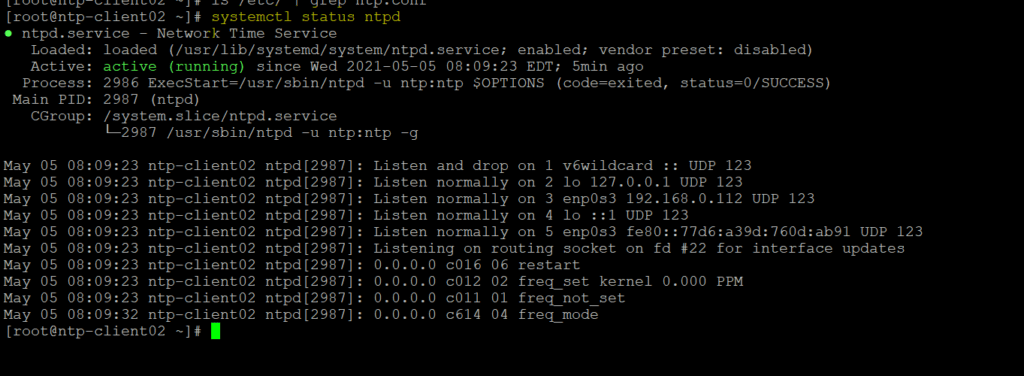
We can now verify /etc/ntp.conf file is copied on both remote machines which is having NTP server name. We can see /etc/ntp.conf file is successfully copied to both remote machines which was not there before running playbook.
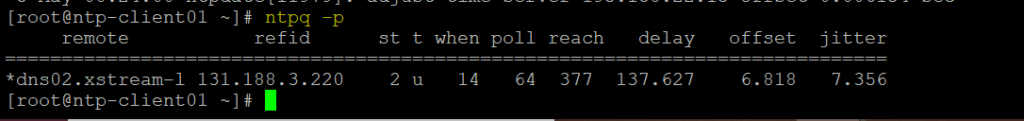
After NTP daemon has been started, wait a few minutes for the server to synchronize time with its pool list servers, then run the following commands to verify NTP peers synchronization status and your system time.




Thanks for the insightful information. If there was already an NTP ugrade on servers, what will be a way to use Ansible just to automate/check to see if The NTP Status is correct for every device?