Introduction
Apparmor is an LSM (Linux Security Module) that allows us to restrict applications’ capabilities with per-program profiles. It supplements the traditional Unix Discretionary Access Control (DAC) model by providing Mandatory Access Control (MAC). It can be seen as an easier alternative to NSA’s SELinux.
In this article, I go over the basic setup of apparmor. The credits for the documentation go to the Arch Wiki.
Enabling AppArmor
Apparmor is compiled in by default on most Linux distributions’ kernel. To enable it on every boot, we need to add it to our kernel boot parameters. SInce I’m using GRUB, I should modify the GRUB_CMDLINE_LINUX parameter in the /etc/default/grub file. The following screenshot shows my GRUB configuration with the required change highlighted:
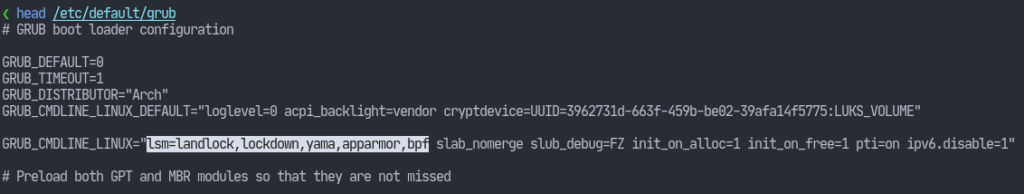
Now run the following command:# grub-mkconfig -o /boot/grub/grub.cfg
The userspace utilities to interact with this module are available via the apparmor package. So run:# pacman -Syu apparmor
We can also enable the corresponding service so that profiles are loaded on boot.# systemctl enable apparmor
Now reboot.
Then, we can check if apparmor was successfully loaded by running the aa-enabled command which should output “Yes”.
Loading AppArmor Profiles
Just enabling the module will serve no purpose. We need to define profiles according to the restrictions we want to place on our programs. Although creating profiles is well documented on the Internet. However, it is rather a tedious task considering the number of applications we usually have on our systems. Fortunately, the installed package comes with a few default profiles.
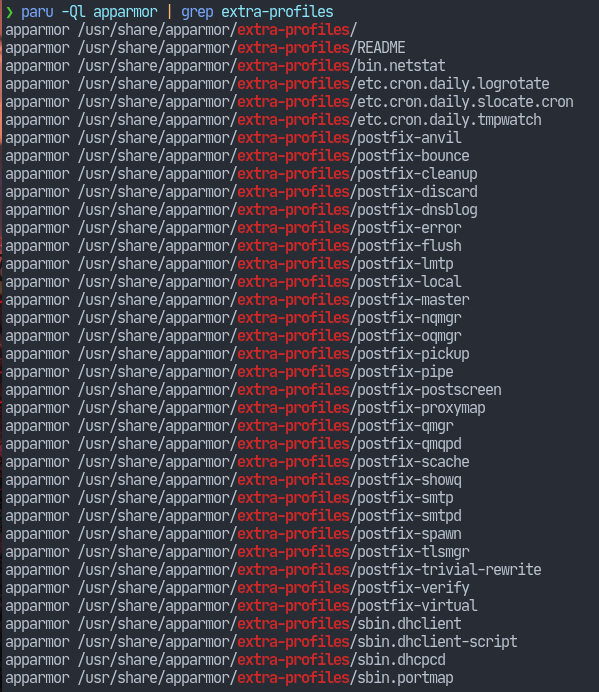
As can be seen with the screenshot, the profiles are located at /usr/share/apparmor/extra-profiles/ directory. However, these profiles need to be parsed, which will then be placed in the /etc/apparmor.d/ directory. This directory contains the profiles that will be loaded into the kernel.
We can use the apparmor_parser(8) utility to parse the profiles under the extra-profiles directory.
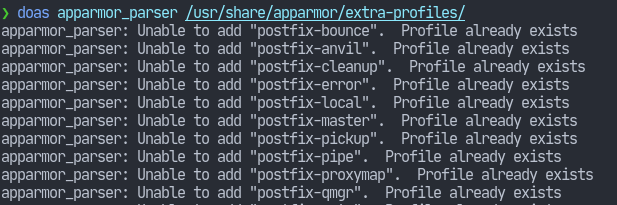
In my case, I had already run the command. So, it displays the obvious message i.e. “Profile already exists”. Nonetheless, when that command finishes, we should now have a few profiles loaded. Use aa-status to view the loaded profiles.
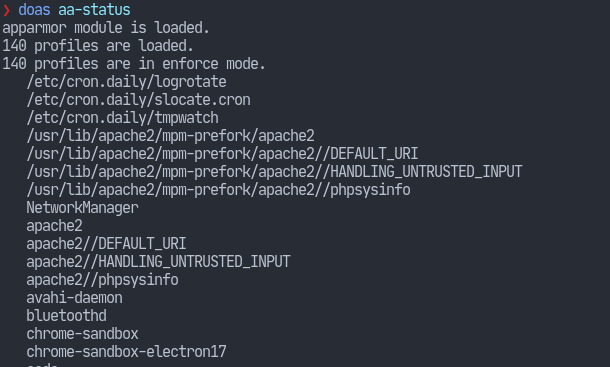
One of the profiles comes for the Chromium web browser. One of the restrictions apparmor enforces is that the browser won’t be able to access anything besides the Downloades folder in the user’s home directory.
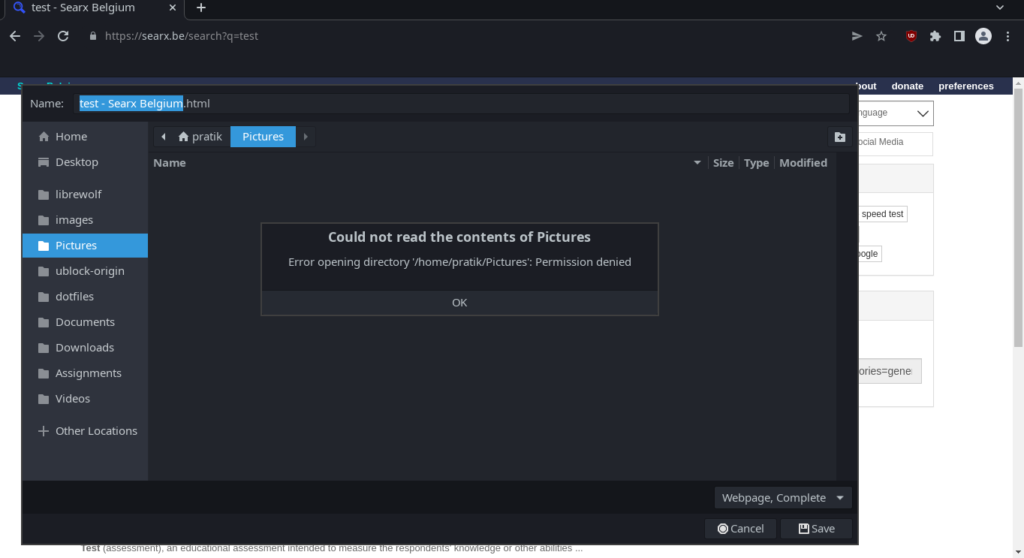
There are also tons of other profiles out in the internet. I will link them down in the references below.
All in all, that should cover the basic usage. I will probably write about generating profiles after a bit more research. Stay tuned!
References
- AppArmor – Arch Wiki
- Creating an AppArmor Profile
- Additional AppArmor Profiles (1)
- Additional AppArmor Profiles (2)



