Today you will learn how to scan Docker Container images.
Introduction
Trivy (tri pronounced like trigger, vy pronounced like envy) is a simple and comprehensive scanner for vulnerabilities in container images, file systems, and Git repositories, as well as for configuration issues. Trivy detects vulnerabilities of OS packages (Alpine, RHEL, CentOS, etc.) and language-specific packages (Bundler, Composer, npm, yarn, etc.).
In addition, Trivy scans Infrastructure as Code (IaC) files such as Terraform, Dockerfile and Kubernetes, to detect potential configuration issues that expose your deployments to the risk of attack. Trivy is easy to use. Just install the binary and you’re ready to scan.
Features
- Comprehensive vulnerability detection
- OS packages (Alpine Linux, Red Hat Universal Base Image, Red Hat Enterprise Linux, CentOS, AlmaLinux, Rocky Linux, CBL-Mariner, Oracle Linux, Debian, Ubuntu, Amazon Linux, openSUSE Leap, SUSE Enterprise Linux, Photon OS and Distroless)
- Language-specific packages (Bundler, Composer, Pipenv, Poetry, npm, yarn, Cargo, NuGet, Maven, and Go)
- Misconfiguration detection (IaC scanning)
- A wide variety of built-in policies are provided out of the box
- Kubernetes, Docker, Terraform, and more coming soon
- Support custom policies
- A wide variety of built-in policies are provided out of the box
- High accuracy
- Support multiple targets
- container image, local filesystem and remote git repository
Installation
On CenTOS
- Install Trivy on CentOS from its repo, so add the repo of trivy then install it as follows:
echo -e "\n[trivy]\nname=Trivy repository\nbaseurl=https://aquasecurity.github.io/trivy-repo/rpm/releases/\$releasever/\$basearch/\ngpgcheck=0\nenabled=1" | sudo tee -a /etc/yum.repos.d/kubernetes.repo
sudo yum -y install trivy- Or install trivy from its RPM source, you will need to get the latest Trivy release then run :
wget https://github.com/aquasecurity/trivy/releases/download/v0.23.0/trivy_0.23.0_Linux-64bit.rpm
sudo yum localinstall ./trivy_0.23.0_Linux-64bit.rpmOn Ubuntu
- From repository
sudo apt-get install wget apt-transport-https gnupg lsb-release
wget -qO - https://aquasecurity.github.io/trivy-repo/deb/public.key | sudo apt-key add -
echo deb https://aquasecurity.github.io/trivy-repo/deb $(lsb_release -sc) main | sudo tee /etc/apt/sources.list.d/trivy.list
sudo apt-get update
sudo apt-get install trivy- From Debian source, you will need to get the latest Trivy release too as we did in CentOS then run the commands below:
wget https://github.com/aquasecurity/trivy/releases/download/v0.23.0/trivy_0.23.0_Linux-64bit.deb
sudo apt install ./trivy_0.23.0_Linux-64bit.debOn Arch Linux|Manjaro
pikaur -Sy trivy-bin
OR
yay -Sy trivy-binUse Trivy
Scanning a Filesystem and git repos
- Trivy can scan a filesystem (such as a host machine, a virtual machine image, or an unpacked container image filesystem).
trivy fs /home/glassfish/
- To scan a Git repo with trivy
trivy repo https://github.com/aquasecurity/trivyScanning a Container image
- List your images
docker images- Scan it with trivy
trivy image httpd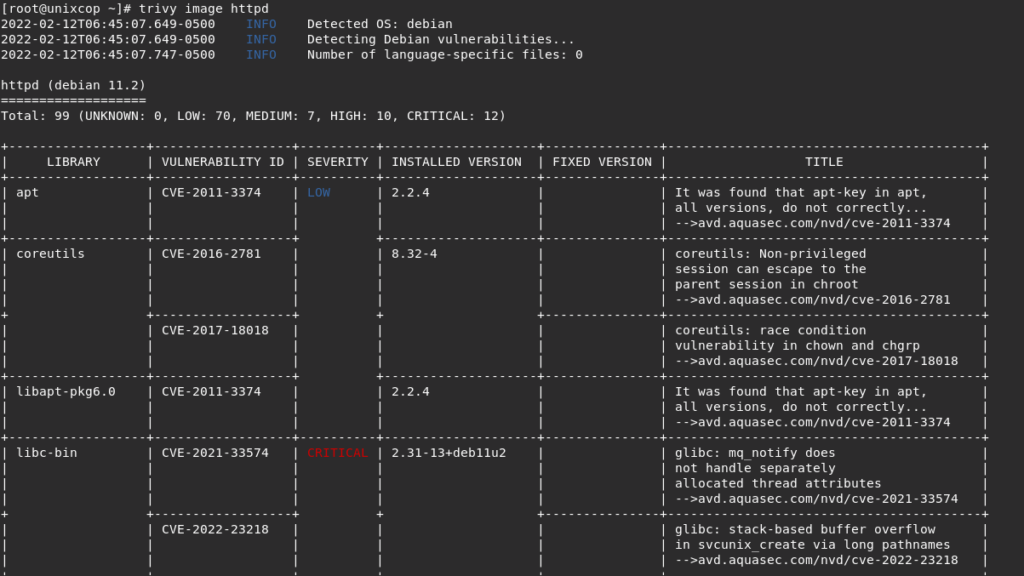
Apply Trivy in Dockerfile
You can include trivy in your Dockerfile and it will scan everything as it builds the image.
For example:
- Create a Dockerfile which contains trivy
vim Dockerfile - Add the following:
FROM alpine:3.7
RUN apk add curl \
&& curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/master/contrib/install.sh | sh -s -- -b /usr/local/bin \
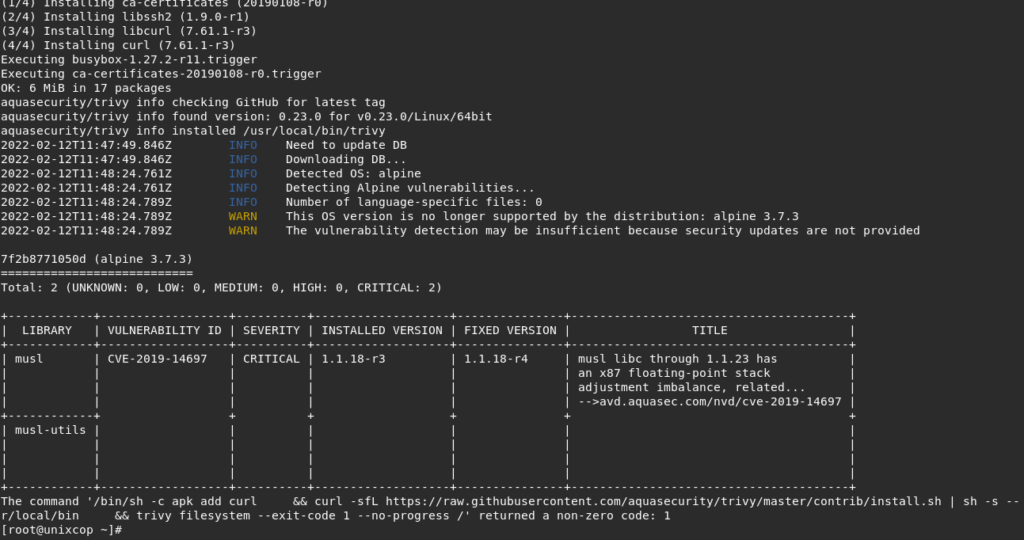
&& trivy filesystem --exit-code 1 --no-progress /- Build the image.
[root@unixcop ~]# docker build -t scanned-image .
Sending build context to Docker daemon 244.6MB
Step 1/2 : FROM alpine:3.7
3.7: Pulling from library/alpine
5d20c808ce19: Pull complete
Digest: sha256:8421d9a84432575381bfabd248f1eb56f3aa21d9d7cd2511583c68c9b7511d10
Status: Downloaded newer image for alpine:3.7
---> 6d1ef012b567
Step 2/2 : RUN apk add curl && curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/master/contrib/install.sh | sh -s -- -b /usr/local/bin && trivy filesystem --exit-code 1 --no-progress /
---> Running in 7f2b8771050d
fetch http://dl-cdn.alpinelinux.org/alpine/v3.7/main/x86_64/APKINDEX.tar.gz
fetch http://dl-cdn.alpinelinux.org/alpine/v3.7/community/x86_64/APKINDEX.tar.gz
(1/4) Installing ca-certificates (20190108-r0)
(2/4) Installing libssh2 (1.9.0-r1)
(3/4) Installing libcurl (7.61.1-r3)
(4/4) Installing curl (7.61.1-r3)
Executing busybox-1.27.2-r11.trigger
Executing ca-certificates-20190108-r0.trigger
OK: 6 MiB in 17 packages
aquasecurity/trivy info checking GitHub for latest tag
aquasecurity/trivy info found version: 0.23.0 for v0.23.0/Linux/64bit
aquasecurity/trivy info installed /usr/local/bin/trivy
2022-02-12T11:47:49.846Z INFO Need to update DB
2022-02-12T11:47:49.846Z INFO Downloading DB...
2022-02-12T11:48:24.761Z INFO Detected OS: alpine
2022-02-12T11:48:24.761Z INFO Detecting Alpine vulnerabilities...
2022-02-12T11:48:24.789Z INFO Number of language-specific files: 0
2022-02-12T11:48:24.789Z WARN This OS version is no longer supported by the distribution: alpine 3.7.3
2022-02-12T11:48:24.789Z WARN The vulnerability detection may be insufficient because security updates are not provided
7f2b8771050d (alpine 3.7.3)
===========================
Total: 2 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 2)
+------------+------------------+----------+-------------------+---------------+---------------------------------------+
| LIBRARY | VULNERABILITY ID | SEVERITY | INSTALLED VERSION | FIXED VERSION | TITLE |
+------------+------------------+----------+-------------------+---------------+---------------------------------------+
| musl | CVE-2019-14697 | CRITICAL | 1.1.18-r3 | 1.1.18-r4 | musl libc through 1.1.23 has |
| | | | | | an x87 floating-point stack |
| | | | | | adjustment imbalance, related... |
| | | | | | -->avd.aquasec.com/nvd/cve-2019-14697 |
+------------+ + + + + +
| musl-utils | | | | | |
| | | | | | |
| | | | | | |
| | | | | | |
+------------+------------------+----------+-------------------+---------------+---------------------------------------+
The command '/bin/sh -c apk add curl && curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/master/contrib/install.sh | sh -s -- -b /usr/local/bin && trivy filesystem --exit-code 1 --no-progress /' returned a non-zero code: 1
[root@unixcop ~]#As shown above, trivy scanned for vulnerabilities for the image included with in the Dockerfile while building.
- You can also filter vulnerabilities by severities with:
trivy image --severity HIGH,CRITICAL httpd:latest
As shown above, we filtered the result for critical and high severities only.
- Scan the container from inside the container
docker run --rm -it nginx \
&& curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/master/contrib/install.sh | sh -s -- -b /usr/local/bin \
&& trivy fs /Conclusion
That’s it
In this guide, We illustrated how to scan Docker Container Images for Vulnerabilities with Trivy in addition to file systems and git repos.
thanks



